Installation of Metasploitable 2
Metasploitable is used by various individuals and organizations, primarily for educational and testing purposes.
What is Metasploitable
Metasploitable is an intentionally vulnerable virtual machine (VM) created by the developers of the Metasploit Framework for testing security tools and conducting penetration testing exercises. It is designed to provide a safe, legal environment for practicing hacking and learning about vulnerabilities in a controlled setting.
Installing Metasploitable 2
Prerequisites
For this, you will need the following:
Installation steps
To start the process, create the virtual machine in VirtualBox by clicking on the New icon at the top and entering the following values in the displayed window:

Click Next, and in the next window, you can leave the RAM value as default, 2048 MB, or assign a bit more if desired.

Click Next, and in the next window, select the option Create a virtual hard disk now

Click on Next and then Finish.

Now, click on the Start button to begin the system installation process.
This process takes around 5 minutes, and you will see the following:
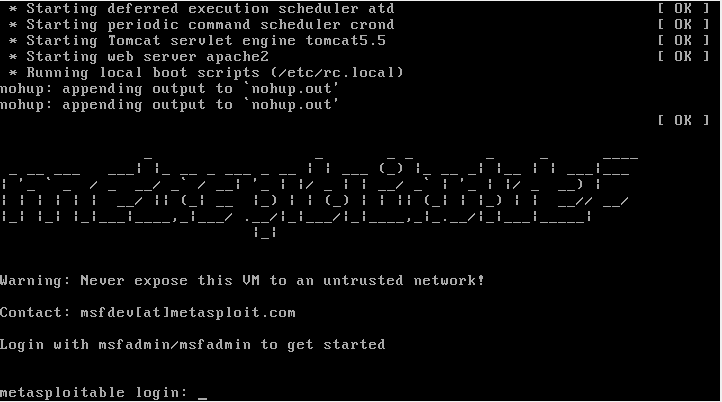
The access credentials are:
1Username: msfadmin 2Password: msfadmin
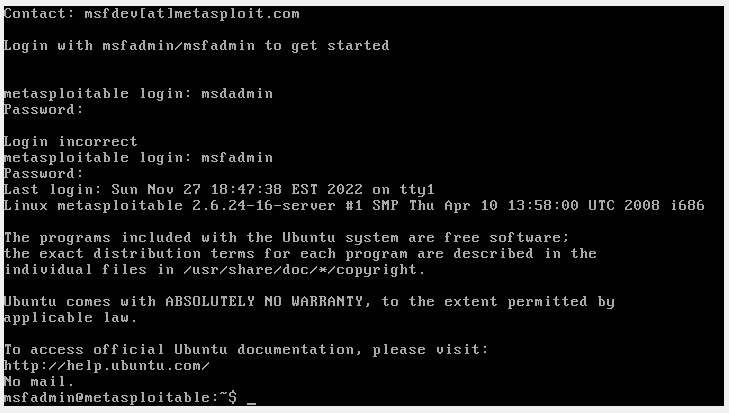
This way, you can use Metasploitable with all the necessary tests.
Common Vulnerabilities in Metasplotailble
Metasploitable is designed with various vulnerabilities, allowing users to practice various exploitation techniques. Some of the most typical vulnerabilities found in Metasploitable include:
1. Weak or Default Credentials:
- SSH (Secure Shell): The SSH service in Metasploitable often uses default or weak credentials, making it susceptible to brute-force attacks.
- FTP (File Transfer Protocol): The FTP server is configured with anonymous access or weak user credentials, which can be easily exploited.
2. Outdated Software:
- Unpatched Services: Many of the services running on Metasploitable are outdated and have known vulnerabilities, making them easy targets for exploitation.
- Apache Tomcat: The Tomcat server running on Metasploitable often has default credentials, allowing attackers to upload malicious code or gain administrative access.
3. Misconfigurations:
- MySQL Database: The MySQL database is often misconfigured, allowing unauthorized access to databases, leading to potential data breaches.
- NFS (Network File System): Misconfigured NFS exports can allow attackers to mount file systems remotely without proper authentication.
4. Web Application Vulnerabilities:
- DVWA (Damn Vulnerable Web Application): This intentionally vulnerable web application includes common web vulnerabilities such as SQL injection, cross-site scripting (XSS), and command injection.
- PHPMyAdmin: An outdated version of PHPMyAdmin is often present with weak credentials, leading to potential database manipulation.
5. Buffer Overflows:
- Vulnerable Daemons: Certain daemons or services are configured to be vulnerable to buffer overflow attacks, allowing attackers to execute arbitrary code or crash the service.
6. Insecure Protocols:
- Telnet: Telnet, an outdated and insecure protocol, is often enabled on Metasploitable, allowing for unencrypted communication and potential credential theft.
- RSH/Rlogin: Remote Shell (RSH) and Remote Login (Rlogin) services are often enabled and insecure, allowing attackers to execute commands on the system remotely.
7. Metasploitable-Specific Vulnerabilities:
- VSFTPD Backdoor: The VSFTPD service in Metasploitable has a backdoor vulnerability, which, when exploited, allows attackers to gain a shell on the system.
- UnrealIRCd Backdoor: An older version of the UnrealIRCd service has a known backdoor that can be exploited to execute arbitrary commands on the server.
8. SMB Vulnerabilities:
- SMB Misconfigurations: The SMB (Server Message Block) service is often configured with vulnerabilities like anonymous access or outdated versions, which can be exploited for unauthorized file access or privilege escalation.
9. Command Injection:
- Vulnerable Web Scripts: Some web scripts in Metasploitable are vulnerable to command injection, allowing attackers to execute system commands through a web interface.
10. Cross-Site Scripting (XSS):
- Web Applications: Various web applications hosted on Metasploitable are vulnerable to XSS, allowing attackers to inject malicious scripts into web pages viewed by other users.
These vulnerabilities are representative of those commonly found in real-world systems, making Metasploitable an effective tool for learning and practicing security testing techniques.