Metasploit pentesting tool
Any pentester needs to be proficient with Metasploit; there is no way around it:
- Comprehensive Toolset: It offers a complete suite of tools for penetration testers, covering the entire lifecycle of a security assessment.
- Community Support: With a large and active community, Metasploit is constantly updated with new exploits and features, making it a cutting-edge tool in the cybersecurity field.
- Educational Value: It’s widely used for learning and training in cybersecurity, making it a foundational tool for anyone pursuing a career in this field.

Metasploit is one of the best open source tools that allow us to locate and exploit security vulnerabilities in systems and services, this tool is essential for pentesting. The most popular project is Metasploit Framework, installed by default in Linux distributions such as Kali Linux. Thanks to the power of Metasploit, we can perform penetration tests to services, applications, and other attacks. It is one of the tools you must have in your arsenal of tools for pen-testing; it complements the other tools we have discussed above. Metasploit has a large community behind it, and tools based on it have been designed to greatly facilitate all tasks by automating them.
Key Components of Metasploit
Exploits
Metasploit contains a vast library of pre-built exploits for known vulnerabilities. An exploit is a piece of code that takes advantage of a security flaw in a system to achieve a certain goal, typically gaining unauthorized access.
Payloads
A payload is the code that runs on the target system after an exploit has been successfully executed. Metasploit includes various payloads, such as:
- Meterpreter: A powerful payload that gives the attacker a command shell with advanced features like file system manipulation, process management, and network pivoting.
- Shell: Provides a simple command shell on the target system.
- Bind and Reverse Shells: Used to connect back to the attacker’s machine or bind a shell to a port on the target.
Auxiliary Modules
These are tools used for scanning, fuzzing, and other tasks that do not involve exploiting a vulnerability directly. Examples include port scanners, service enumerators, and vulnerability scanners.
Post-Exploitation Modules
After successfully exploiting a system, post-exploitation modules help attackers maintain access, escalate privileges, collect information, and more.
Encoders
Encoders modify payloads to evade detection by antivirus software. They obfuscate the payload, making it harder for security systems to recognize it as malicious.
Nops (No-Operation Generators)
Nops are used to pad out payloads to a specific size or to help in creating more stable exploits.
Versions of Metasploit:
- Metasploit Framework: The free and open-source version used by most security professionals and researchers. It is command-line-based and highly flexible.
- Metasploit Pro: A commercial version with a graphical user interface (GUI), automated features, and additional tools for managing large-scale penetration tests and generating reports.
- Metasploit Community Edition: A limited version of Metasploit Pro, aimed at small organizations and individual testers, providing some GUI features but with restrictions.
Metasploit Complementary Tools
Armitage (free)
Armitage is another tool that provides a free visual layer for using Metasploit. With this software you will be able to use Metasploit without the need to use it with commands, everything is done visually. This makes it even easier to use for people who are not familiar with the Metasploit terminal and are learning.
Cobalt Strike (paid)
Cobalt Strike is another visual layer for Metasploit with the difference over Armitage that it is paid. This tool is clearly an improved version of Armitage that allows you to do the same, but with more features and even incorporates other tools to improve its practicality, such as Mimikatz.
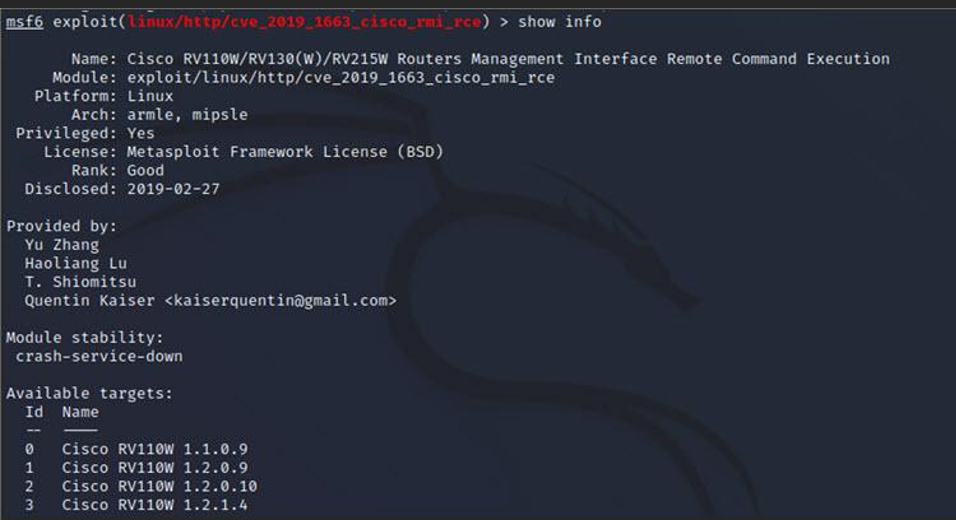
Once the command to start the tool has been executed, we will have access to a command terminal in the tool. Here we will be able to choose among the exploits already loaded for the exploit and select one of them. Then, we must configure parameters specific to the exploit we have chosen, such as, for example, the IP or target ports, HTTP listening servers, and more. Finally, we can start running the exploit.