Pentesting Reconnaissance: Gathering information about the target
Gathering information about the target, also known as the "reconnaissance" or "enumeration" pentesting phase, is a crucial stage in penetration testing and security assessments. Here are general steps and some standard techniques and tools used in this phase:
- Define the Scope: Establish the specific boundaries and objectives of the information gathering, and obtain the consent of the system or network owner.
- Identify Objectives: Determine the specific systems, networks, applications and services to be evaluated during the test.
- Domain Collection: Use techniques such as WHOIS, DNS enumeration, and search engine lookup to collect information on domains associated with the target.
- Subdomain scanning: Use tools such as Sublist3r, Subfinder, or DNSDumpster to identify subdomains associated with the target.
- Mail Server Identification: Search for mail servers associated with the target using DNS resolution techniques and specialized tools.
- Network enumeration: Use techniques such as network scanning, ARP scanning, or SNMP enumeration to identify devices and hosts on the target's network.
- Technology identification: Use tools such as Wappalyzer, BuiltWith or WhatWeb to identify technologies, platforms and services used in the target.
- Web Application Scanning: Identify web applications on the target and obtain information about their technologies, versions and configurations.
Common Information Gathering Tools
- WHOIS Lookup: Obtain information about domain owners and IP addresses.
- Tool: WHOIS (line command), WHOIS websites.
- DNS Enumeration: Identify DNS records, including name servers and associated IP addresses.
- Tool: Dig, NSLookup, DNSRecon.
- Subdomain Enumeration: Identify subdomains associated with the main domain.
- Tool: Sublist3r, Subfinder, DNSDumpster.
- Network Scanning: Identify active hosts and devices on the network.
- Tool: Nmap, Masscan, ARP Scan.
- Web Application Scanning: Identify web applications and their associated technologies.
- Tool: Wappalyzer, BuiltWith, WhatWeb.
- Technology and Version Search: Identify technologies and versions used in the target.
- Tool: Shodan, Censys, Nmap.
The information gathered during this phase provides a solid foundation for the later stages of penetration testing, allowing security professionals to understand the attack surface and target their efforts effectively. It is essential to conduct these activities within ethical and legal boundaries, always obtaining the consent of the system or network owner.
Intelligence gathering on web applications using Kali Linux and web resources
Intelligence gathering is the technique of collecting numerous information about the target. Intelligence gathering is the most important first step in performing penetration testing. Intelligence gathering gives the penetration tester a gateway to decide what vulnerabilities are commonly found in specific web applications. There are many tools for gathering information in Kali Linux. In this tutorial, we will learn specifically how to gather information from web applications such as Whois, Whatweb, NSLookup and CMSeek. These tools are open source and are already pre-installed in Kali Linux. If you don't have Kali Linux, you can download or review these tool projects on GitHub.
Links are provided in each tool section below. Information gathering can be divided into two methods: active information gathering and passive information gathering. When actively gathering information, the hacker contacts the target. For example, use a payload designed to evaluate how a particular web application would respond. While passively collecting information, the hacker uses a third-party program to do the job, for example, using the OSINT technique to collect a lot of information available on the Internet. Given this simple definition, you will immediately know which information gathering tools we are going to use below are categorized. We will learn about the following topics in detail:
- Type of information collected during the information gathering phase.
- Detailed domain name ownership information
- Identifying the IP address of the name server
Before a penetration tester gathers information, first define the target. Different categories of targets use different techniques and appropriate tools. For example, if your target is a wireless network, the techniques used to gather information about web applications may not apply. Kali Linux is a powerful Linux distribution that provides open source tools for various information gathering tasks.
WHOIS
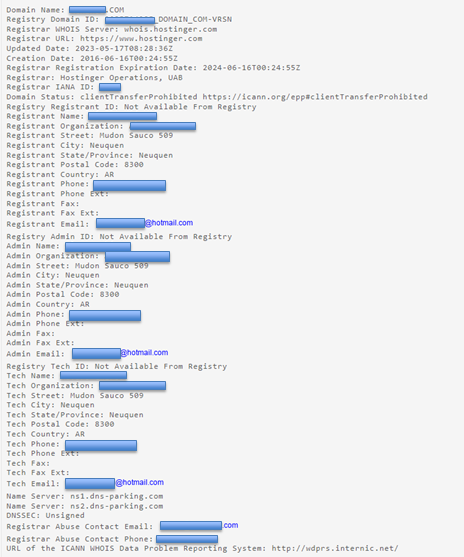
GitHub: https://github.com/rfc1036/whois WHOIS is a TCP-based transactional query and response protocol commonly used to provide domain name ownership information, e.g. registration date or domain creation date and expiration date, name servers and registrant contact information (address, phone and mail). Some domain registration providers or companies may offer a service to hide registration information.
Whois comes pre-installed in Kali Linux, it can also be found on the web. I often use Whois in Kali Linux and Whois online to see if there is any difference in information between them. In this tutorial we will definitely cover Whois in Kali Linux. Let's take a look at using the Whois command in the Kali Linux terminal below:
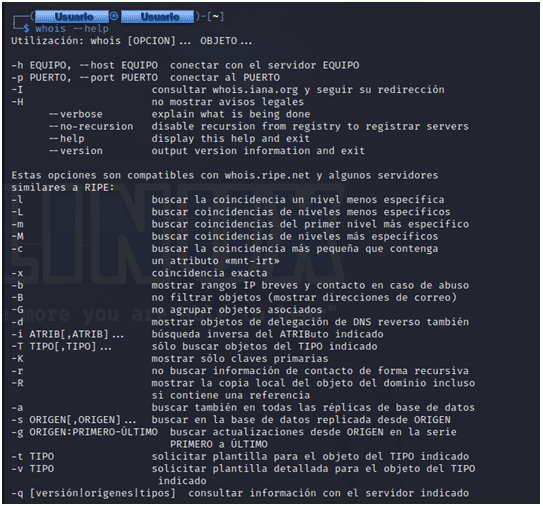
Using the Whois command in Kali Linux To run Whois in Kali Linux, enter the following command pattern: You can add "-verbose" to the end of the command to display more detailed information. Remember to type [domain-name] without protocol type neither HTTP nor HTTPS. For example: The following example is the result of the domain information with Whois that is publicly available.
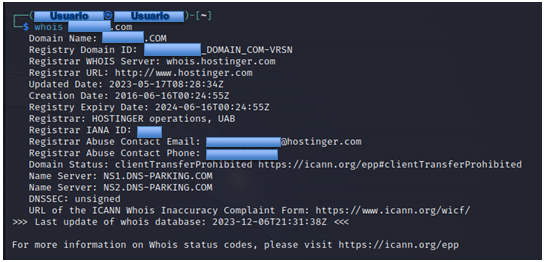
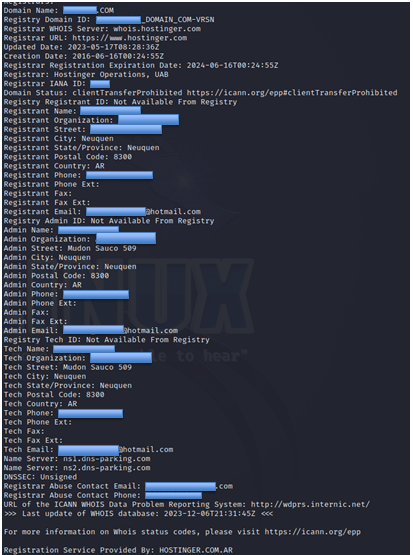
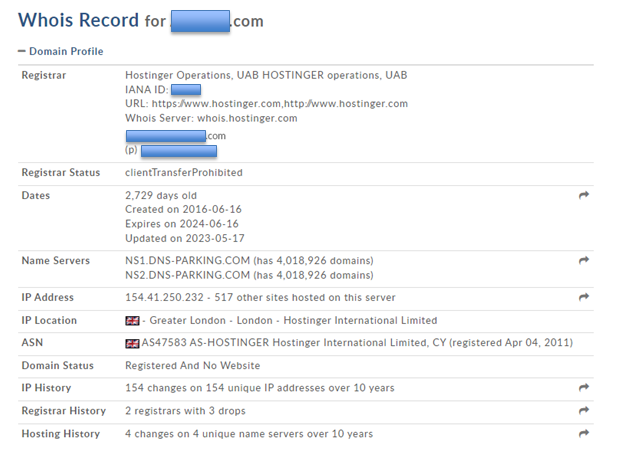
Whois registrant information As shown above, we have been able to get a lot of detailed information about the domain name ownership such as: Creation date, registrant name, address, phone number and email address. To save the output information from the terminal or text file, you can add an output redirection operator ('>>') followed by the file name and file type. Using this operator at the end of each command means that any output intended to be displayed on the terminal will also be saved to a text file. Whois domain >> whois_Domain.txt Now notice how the domain name registrant uses a private service to display its whois information.
You can also get information with this web tool: https://whois.domaintools.com/
Nslookup
NSlookup, short for name server lookup, is a network management tool for querying Internet domain name system details, such as IP address record, MX (mail server) record, name server, SOA (start of authority) record, and TXT record. NSLookup is a standard program for all operating systems. NSLookup also comes with an online version. There are so many websites that offer a NSLookup program.
Find out the "A" record (IP address) of the domain.
- # nslookup
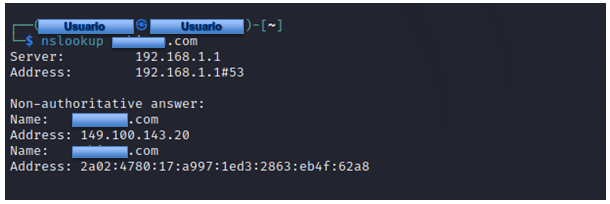
- # nslookup google.com
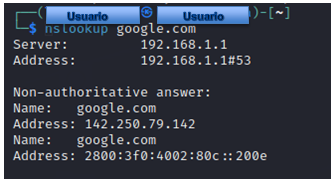
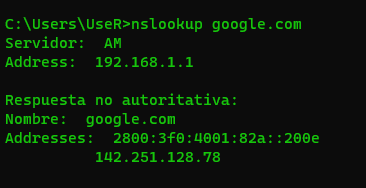
Discover reverse domain lookup
- # nslookup 142.250.79.142
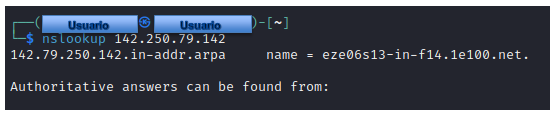
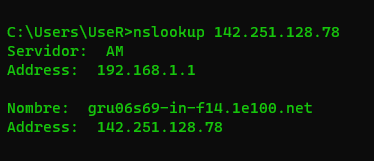
ViewDNS
The tools provided by ViewDNS.info allow users to collect a large amount of data about a given website or IP address. The value of this data can sometimes be underestimated when analyzed in its raw form, but when placed in context it can be quite powerful. This section is intended to demonstrate some of the information that can be discovered using the tools available on this site.
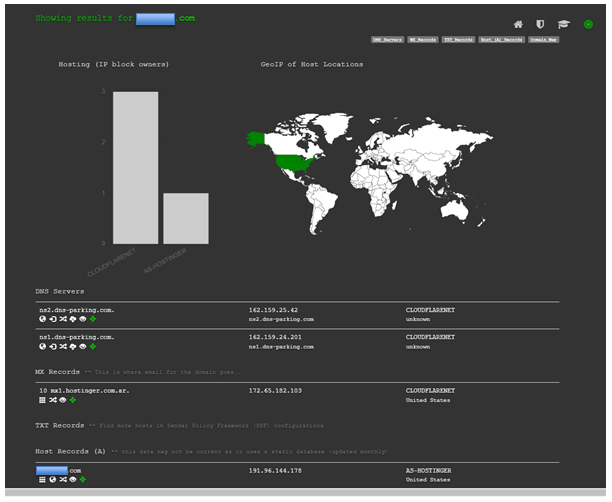
DNSdumpster
DNSdumpster.com is a FREE domain research tool that can discover hosts related to a domain. Finding hosts visible from the attackers' perspective is an important part of the security assessment process.
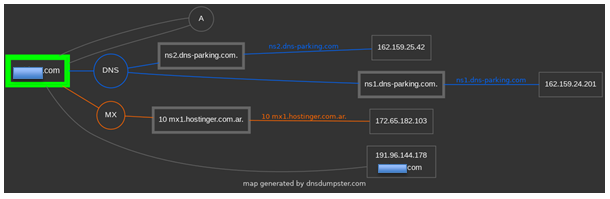
Sitemap
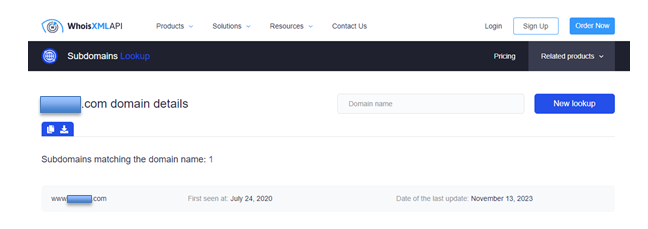
Sub domain search
Subdomain search tools allow you to discover the subdomains of any target domain to uncover potential attack entry points. Find the systems that are least protected and therefore most vulnerable to attack.
https://subdomains.whoisxmlapi.com/
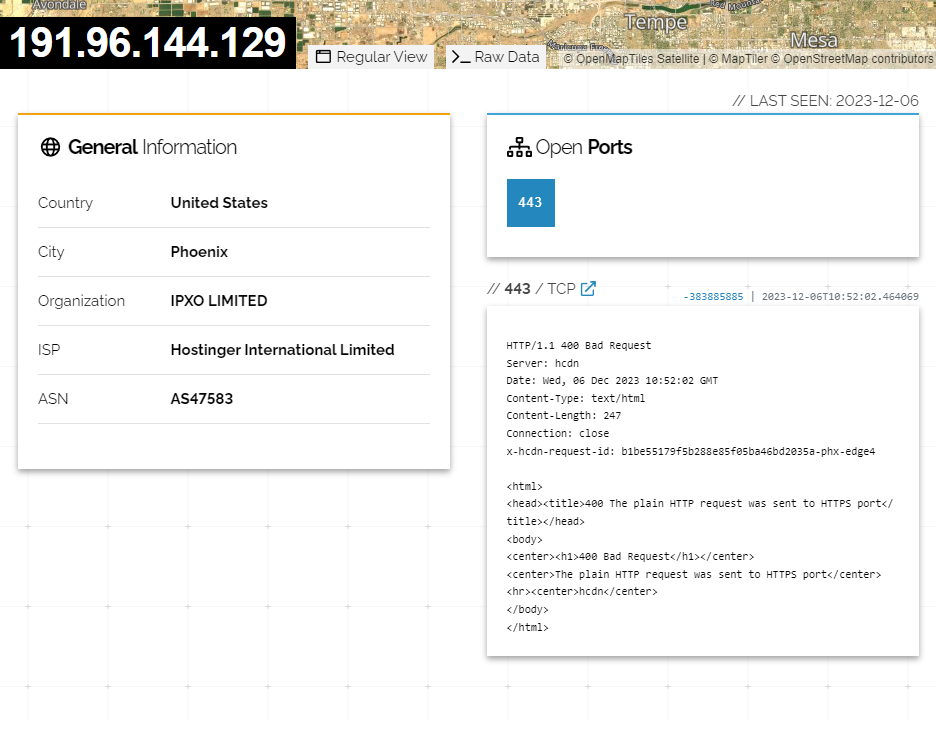
Shodan
Shodan is the world's first search engine for Internet-connected devices. Discover how Internet intelligence can help you make better decisions.
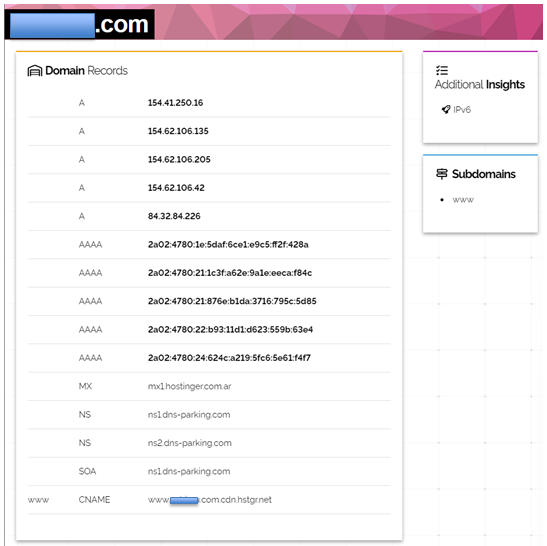
https://www.shodan.io/host/191.96.144.129
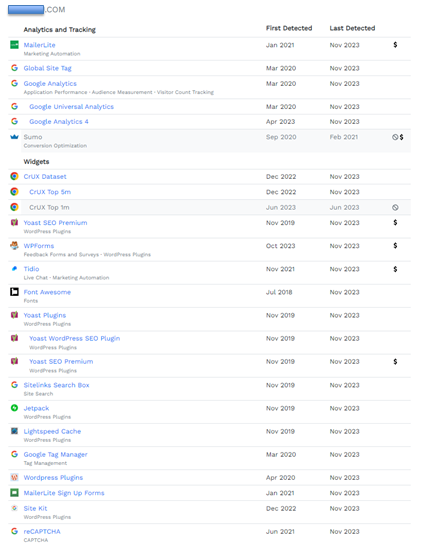
BuiltWith
BuiltWith is a website profiling, lead generation, competitive analysis and business intelligence tool that provides technology adoption, e-commerce data and Internet usage analysis.
BuiltWith's technology tracking includes widgets, analytics, frameworks, content management systems, advertisers, content delivery networks, web standards and web servers, to name a few of the technology categories we cover.
SSL server testing
This free online service performs an in-depth analysis of the configuration of any SSL web server on the Internet.
