NoSQL Injection
One of the most infamous NoSQL injection attacks occurred in 2018 when a major data breach at the company Exactis resulted in the exposure of 340 million user records. This breach was caused by a NoSQL Injection vulnerability, which allowed attackers to manipulate the database queries and gain unauthorized access to sensitive information.
What is NoSQL Injection?
NoSQL injection is a type of injection attack that targets NoSQL databases, such as MongoDB, CouchDB, and Redis. Unlike traditional SQL injection, which targets SQL databases, NoSQL injection exploits vulnerabilities in the way NoSQL databases process untrusted input.
In a NoSQL injection attack, an attacker can manipulate a query to execute arbitrary commands or retrieve unauthorized data. This is often achieved by inserting malicious code into the query parameters, which the database then executes. The lack of a standardized query language in NoSQL databases means that the specific techniques for injection can vary widely depending on the database being targeted.
For information on SQL injection, which is a similar but distinct type of attack, see our SQL Injection guide.
How NoSQL Injection Works
NoSQL injection typically occurs when an application fails to properly sanitize user input before including it in a database query. Here are some common scenarios where NoSQL injection can occur:
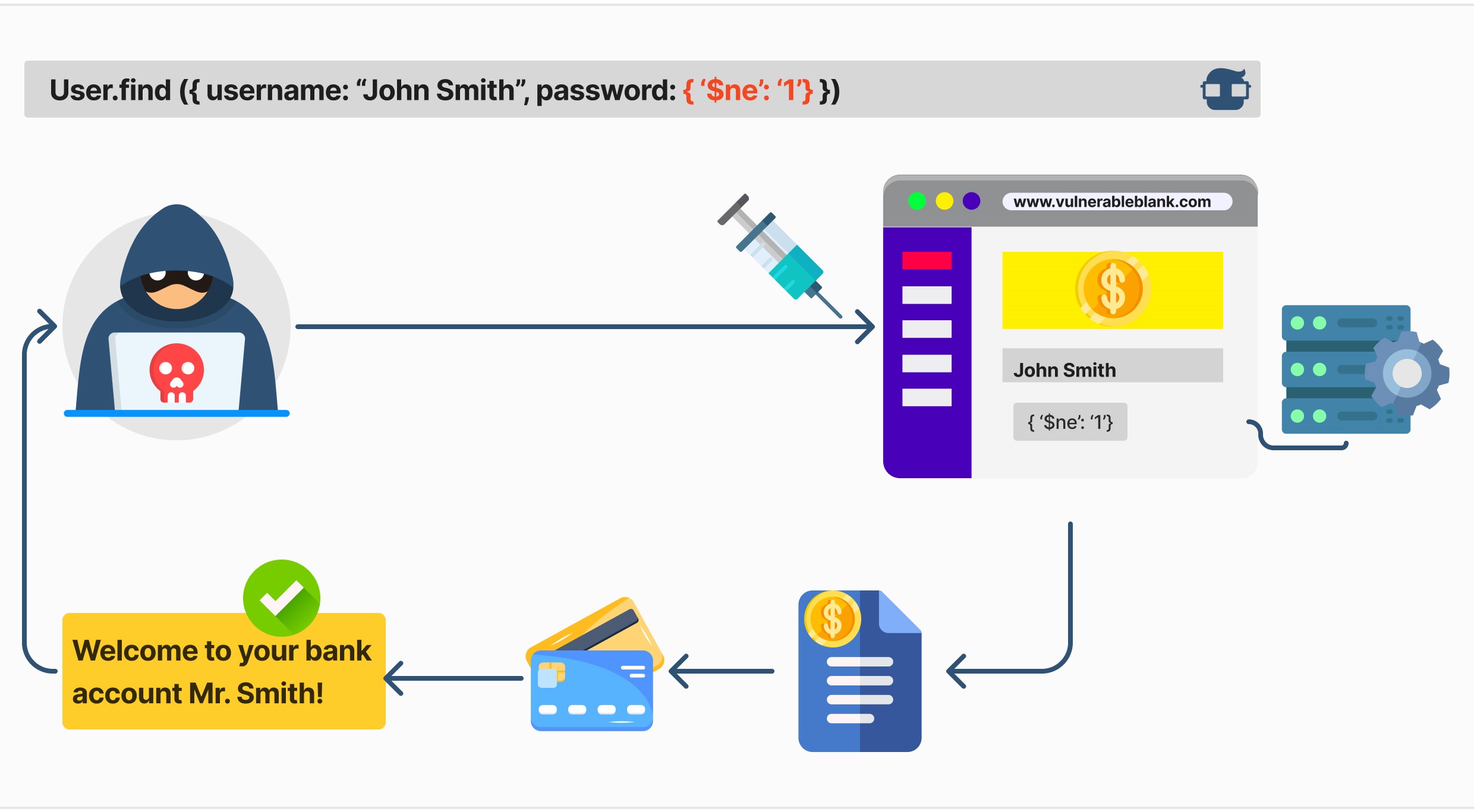
1. User Authentication Bypass
An attacker can manipulate the login credentials to bypass authentication checks. For example, in a MongoDB query, an attacker might use the following payload to bypass authentication:
1{ 2 "username": {"$ne": null}, 3 "password": {"$ne": null} 4}
This payload exploits the $ne (not equal) operator to match any document where the username and password fields are not null, effectively bypassing the authentication check.
2. Data Retrieval
An attacker can manipulate query parameters to retrieve unauthorized data. For example, an attacker might use the following payload to retrieve all documents in a collection:
1{ 2 "$where": "this.age > 25" 3}
This payload uses the $where operator to execute a JavaScript expression on the server, allowing the attacker to retrieve documents where the age field is greater than 25.
3. Data Manipulation
An attacker can manipulate query parameters to modify or delete data. For example, an attacker might use the following payload to update all documents in a collection:
1{ 2 "$set": {"isAdmin": true} 3}
This payload uses the $set operator to update the isAdmin field to true for all documents in the collection.
Preventing NoSQL Injection
To prevent NoSQL injection, it is important to implement the following security measures:
- Input Validation: Validate and sanitize all user input to ensure that it does not contain malicious code. Use whitelisting techniques to allow only known good input.
- Parameterized Queries: Use parameterized queries or prepared statements to separate user input from the query logic. This helps prevent the injection of malicious code.
- Access Controls: Implement strict access controls to limit the permissions of users and applications. Ensure that only authorized users have access to sensitive data and operations.
- Security Audits: Regularly perform security audits and code reviews to identify and fix vulnerabilities in the application and database configuration.
- Update and Patch: Keep the database and application software up to date with the latest security patches and updates.
The consequences of a NoSQL Injection can be severe and varied, depending on the type of data stored in the database and the attackers' ability to exploit the vulnerability.
Tools for Detecting NoSQL Injection Vulnerabilities
Detecting NoSQL injection vulnerabilities in a web application can be challenging, but there are several tools and techniques that can help identify these security issues:
-
Burp Suite: Burp Suite is a popular web vulnerability scanner that can be used to detect NoSQL injection vulnerabilities. It allows for manual and automated testing of web applications and can identify various types of injection flaws.
-
OWASP ZAP (Zed Attack Proxy): OWASP ZAP is an open-source web application security scanner that can be used to find NoSQL injection vulnerabilities. It provides automated scanners as well as tools for manual testing.
-
NoSQLMap: NoSQLMap is an open-source tool specifically designed to detect and exploit NoSQL injection vulnerabilities. It supports various NoSQL databases, including MongoDB, CouchDB, and Redis.
-
Nmap with NSE Scripts: Nmap is a network scanning tool that can be extended with NSE (Nmap Scripting Engine) scripts to detect NoSQL injection vulnerabilities. Custom scripts can be written or existing ones can be used to identify potential issues.
-
SQLMap: Although primarily designed for SQL injection, SQLMap can also be used to detect NoSQL injection vulnerabilities with some modifications and custom scripts.
-
Manual Testing: Manual testing techniques, such as input fuzzing and code review, can be effective in identifying NoSQL injection vulnerabilities. Security testers can manually craft payloads to test for injection flaws and review the application's code for potential vulnerabilities.
By using these tools and techniques, security professionals can identify and mitigate NoSQL injection vulnerabilities in web applications, helping to protect sensitive data and maintain the integrity of the application.