ISMS
risk assessment
cybersecurity
ISO 27001
ISMS Framework Implementation and Risk Assessment
ISMS Framework Implementation and Risk Assessment
If you want to get certified for ISO 27001, you need to have an ISMS in place. This document explains the framework and how to implement it.
An Information Security Management System (ISMS) is a systematic approach to managing sensitive company information so that it remains secure. It includes people, processes and IT systems by applying a risk management process.
ISMS Framework Components
The ISMS framework consists of the following key components:
- Information Security Policies.
- Organization of Information Security.
- Human Resource Security.
- Asset Management
- Access Control.
- Cryptography.
- Physical and Environmental Security.
- Operations Security.
- Communications Security
- System Acquisition, Development and Maintenance.
- Supplier Relationships.
- Information Security Incident Management.
- Business Continuity Management.
- Compliance.
These components work together to create a comprehensive approach to managing and protecting an organization's sensitive information across people, processes, and IT systems.

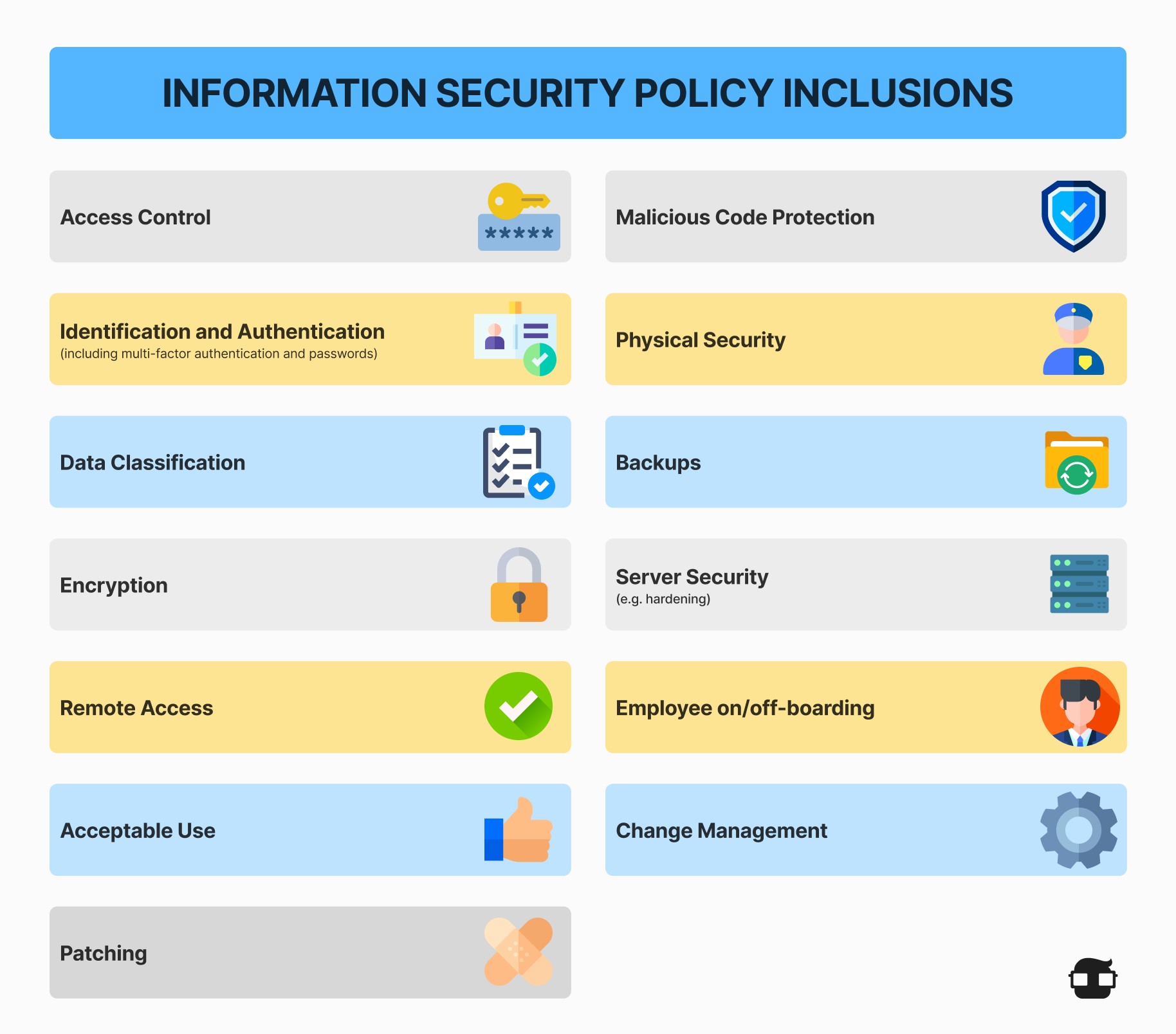
Information Security Policies
Overarching guidelines that define the organization's approach to information security. For example:
- Policy Statement: A high-level statement that outlines the organization's commitment to information security.
- Scope: Defines which parts of the organization are covered by the ISMS.
- Roles and Responsibilities: Assigns specific roles and responsibilities for information security.
- Procedures: Provides detailed procedures for implementing and maintaining the ISMS.
- Review and Update: Outlines the process for reviewing and updating the ISMS.
Organization of Information Security
Defines roles and responsibilities for information security within the organization. For example:
- Information Security Committee: A group of senior managers responsible for overseeing the ISMS.
- Information Security Officer (ISO): A designated individual responsible for implementing and maintaining the ISMS.
- Information Security Team: A group of individuals responsible for specific aspects of the ISMS.
Human Resource Security
Ensures that employees understand their responsibilities and are suitable for their roles. For example:
- Employee Training: Provides training for employees on information security policies and procedures.
- Employee Screening: Conducts background checks on employees who handle sensitive information.
- Employee Termination: Implements procedures for terminating employees who pose a security risk.
Asset Management
Identifies organizational assets and defines appropriate protection responsibilities. For example:
- Asset Identification: Identifies all valuable assets within the scope of the ISMS.
- Asset Classification: Assigns a level of importance to each asset based on its value to the organization.
- Asset Protection: Defines the appropriate security measures for each asset.
Access Control
Limits access to information and information processing facilities. For example:
- Access Control Policies: Defines who can access specific assets and what they can do with them.
- Authentication: Verifies the identity of users before granting access.
- Authorization: Limits access to only what is necessary for the user's role.
- Auditing: Monitors and logs all access attempts.
Cryptography
Ensures proper and effective use of cryptography to protect information confidentiality, authenticity and/or integrity. For example:
- Encryption: Encrypts data to prevent unauthorized access.
- Digital Signatures: Verifies the authenticity of data by using digital signatures.
- Key Management: Manages cryptographic keys to ensure secure use.
Physical and Environmental Security
Prevents unauthorized physical access, damage, and interference to the organization's information and information processing facilities. For example:
- Physical Security: Defines measures to secure physical assets, such as buildings, equipment, and storage areas.
- Environmental Security: Ensures that the physical environment is suitable for information security, such as temperature and humidity control.
Operations Security
Ensures correct and secure operations of information processing facilities. For example:
- Change Management: Controls changes to information systems to prevent disruptions.
- Incident Response: Defines procedures for responding to security incidents.
- Backup and Recovery: Implements procedures for backing up and recovering information.
Communications Security
Protects information in networks and its supporting information processing facilities. For example:
- Firewalls: Restricts access to networks to authorized users.
- Intrusion Detection Systems: Monitors network traffic for suspicious activity.
- Encryption: Encrypts data in transit to prevent unauthorized access.
System Acquisition, Development and Maintenance
Ensures that information security is an integral part of information systems across the entire lifecycle. For example:
- Security Requirements: Defines security requirements for new systems.
- Security Testing: Conducts security testing of new systems.
- Security Training: Provides training for employees who develop or maintain systems.
Supplier Relationships
Ensures protection of the organization's assets that are accessible by suppliers. For example:
- Supplier Security Requirements: Defines security requirements for suppliers.
- Supplier Security Training: Provides training for suppliers on information security policies and procedures.
- Supplier Security Audits: Conducts security audits of suppliers.
Information Security Incident Management
Ensures a consistent and effective approach to the management of information security incidents. For example:
- Incident Response Plan: Defines procedures for responding to security incidents.
- Incident Reporting: Defines who is responsible for reporting security incidents.
- Incident Investigation: Defines procedures for investigating security incidents.
- Incident Recovery: Defines procedures for recovering from security incidents.
Information Security Aspects of Business Continuity Management
Ensures the continuity of information security management in adverse situations. For example:
- Business Continuity Plan: Defines procedures for maintaining information security in the event of a disaster.
- Disaster Recovery Plan: Defines procedures for recovering from a disaster.
- Backup and Recovery: Implements procedures for backing up and recovering information.
Compliance
Avoids breaches of legal, statutory, regulatory or contractual obligations related to information security. For example:
- Compliance Requirements: Defines the legal, statutory, regulatory or contractual obligations related to information security.
- Compliance Monitoring: Monitors compliance with these requirements.
- Compliance Reporting: Reports compliance with these requirements.
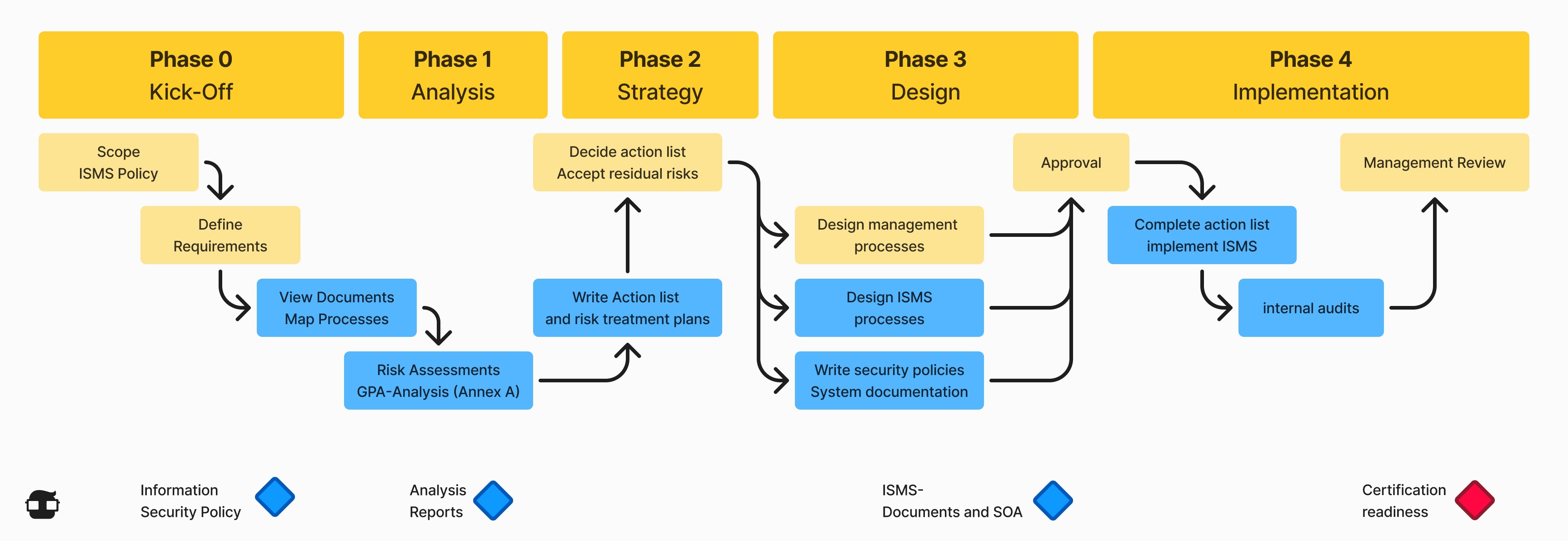
ISMS Implementation Process
Now that we know the framework, let's look at the process of implementing an ISMS.The implementation of an ISMS typically follows these steps:
1) Define the Scope
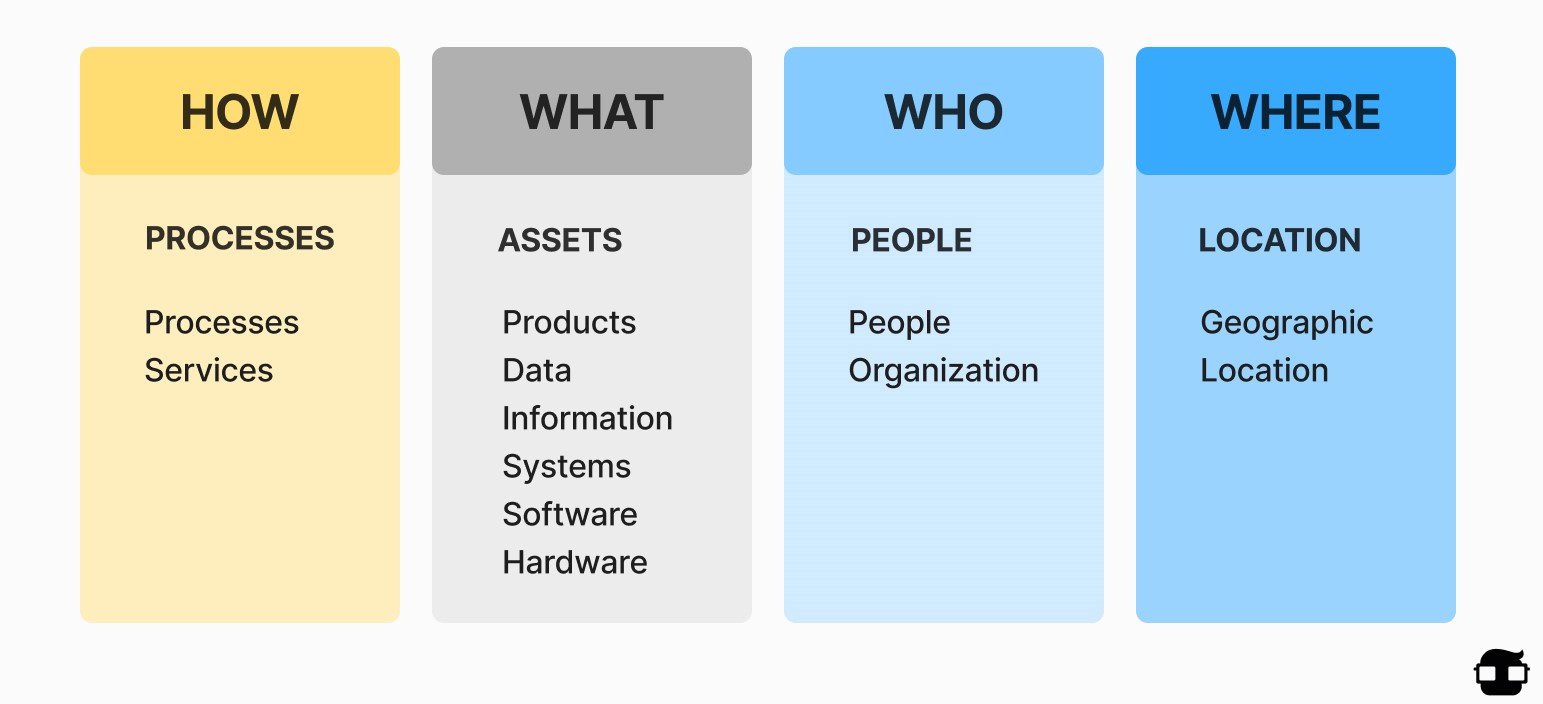
Determine which parts of the organization will be covered by the ISMS. To better understand the scope, you can use How, What, Who, Where:
- How: How will the ISMS be implemented?
- What: What will the ISMS cover? Assets, Data, Information systems, Software, Hardware, etc.
- Who: People and organizations involved in the ISMS.
- Where: Geographical areas covered by the ISMS.
Another set of questions you can use to define the scope is:
- What type of information is processed, stored or transmitted by the organization?
- What are the critical assets of the organization?
- What are the vulnerabilities of the organization?
- What are the threats to the organization?
- What are the impacts of the threats to the organization?
- What are the risks to the organization?
- What are the controls to the organization?
Keep in mind that in order to get certified, the ISMS must be implemented in the whole organization.
2) Develop an Information Security Policy
Create a high-level document that outlines the organization's approach to information security. The following table of contents is a good starting point:
- Introduction: Provides an overview of the ISMS and its purpose.
- Scope: Defines which parts of the organization are covered by the ISMS.
- Roles and Responsibilities: Assigns specific roles and responsibilities for information security.
- Procedures: Provides detailed procedures for implementing and maintaining the ISMS.
- Review and Update: Outlines the process for reviewing and updating the ISMS.
3) Conduct a Risk Assessment
Identify, analyze, and evaluate information security risks. With all the knowledge gained from pentesting, DLP scans, and other sources, you should have a good understanding of the risks. Use this matrix to structure the risk assessment:

4) Develop a Risk Treatment Plan
This is what you can do with a risk: Accept, Avoid, Transfer, Mitigate, Monitor.Decide how to address the identified risks.
- Accept a risk if the risk is low.
- Avoid a risk if it's not possible to mitigate it.
- Transfer a risk if you can get someone else to mitigate it.
- Mitigate a risk if you can't avoid it.
- Monitor a risk if you accept it or transfer it.

5) Select and Implement Controls
Choose and implement appropriate security controls based on the risk assessment and treatment plan.
6) Train Staff
Ensure all relevant personnel are aware of their roles and responsibilities in maintaining information security. Some examples of training are:
- Security Awareness Training: Provides training for employees on information security policies and procedures.
- Security Training for New Employees: Provides training for new employees on information security policies and procedures.
- Regular Security Audits: Conducts regular security audits of employees.
7) Monitor and Review
Continuously monitor and approve the effectiveness of the ISMS and make improvements as necessary, including managment review! To achieve this, you can:
- Regular Internal Audits: Name a person or team to conduct regular internal audits of the ISMS. Make sure they are independent and have the authority to report to the top management.
- Regular External Audits: Hire an external auditor to conduct regular external audits of the ISMS on a regular basis.
- Management Review: Involves top management in the review of the ISMS. Schedule a recurring meeting with the top management to review the KPIs and propose improvements.
You have to choose your KPIs (Key Performance Indicators) based on the risk assessment and the risk treatment plan. For example:
- Number of security incidents
- Number of compliance violations
- Time to detect and respond to security incidents
- Time to detect and respond to compliance violations
- Number of security incidents per year
- Number of compliance violations per year
- Number of security incidents per year
Risk Assessment Methodologies
ISO 27001 doesn't prescribe a specific risk assessment methodology, but some common approaches include:
-
Qualitative Risk Analysis: Uses predefined scales (e.g., low, medium, high) to assess the likelihood and impact of risks.
-
Quantitative Risk Analysis: Uses numerical values to assess risks, often in terms of financial impact.
-
OCTAVE (Operationally Critical Threat, Asset, and Vulnerability Evaluation): A method that focuses on organizational risk and strategic, practice-related issues.

- FAIR (Factor Analysis of Information Risk): A model for understanding, analyzing, and measuring information risk.
Identifying and Evaluating Risks
The risk identification and evaluation process typically involves:
-
Asset Identification: List all valuable assets within the scope of the ISMS.
-
Threat Identification: Determine potential threats to these assets.
-
Vulnerability Assessment: Identify weaknesses that could be exploited by threats.
-
Impact Analysis: Assess the potential consequences if a threat exploits a vulnerability.
-
Likelihood Assessment: Estimate the probability of a threat exploiting a vulnerability.
-
Risk Calculation: Combine impact and likelihood to determine the overall risk level.
Risk Treatment Strategies
ISO 27001 outlines four main risk treatment options:
-
Risk Modification: Implement controls to reduce the risk.
-
Risk Retention: Accept the risk as it is, if it falls within the organization's risk appetite.
-
Risk Avoidance: Eliminate the risk by removing the risk source or discontinuing the activity.
The chosen strategy should be documented in a risk treatment plan, which outlines the selected controls, responsibilities, and timelines for implementation.
By following this framework and these methodologies, organizations can establish a robust ISMS that effectively manages information security risks in compliance with ISO 27001.