Data Security and Privacy
Generally speaking, data security and privacy refer to protective measures for digital privacy that are applied to prevent unauthorized access to data on computers, databases, websites, etc. Data security also protects data from possible corruption.
What is Data Security and Privacy?
Data security and privacy, also known as information security or computer security, is an essential aspect of IT for organizations of any size and type.
It involves protecting data against unauthorized access and safeguarding it from possible corruption throughout its lifecycle.
Data security includes concepts such as data encryption, tokenization, and key management practices that help protect data across all applications and platforms within an organization.
Today, organizations worldwide invest heavily in IT technologies related to cyber defense to protect their critical assets: their brand, intellectual property, and customer information.
In all data security topics, there are common elements that all organizations must consider when implementing their measures:
-
People: This refers to the importance of users and employees within the organization. It includes training and raising awareness about security practices, creating a culture of security, and implementing policies to ensure that individuals understand and follow security guidelines.
-
Processes: This refers to the procedures and policies established to manage and protect data. It includes creating security protocols, defining roles and responsibilities, conducting regular audits, and managing incidents to ensure all aspects of data security are addressed systematically and organized.
-
Technology: This refers to the tools and systems used to protect data. It includes using antivirus software, firewalls, intrusion detection systems, data encryption, and any other technology that helps protect data against unauthorized access and cyberattacks.
Data security
In a connected digital world, Information Security stands as the bulwark that guards the secrets, privacy, and integrity of our data. Ensuring data security and privacy is crucial in protecting this information.
This article explores the essential fundamentals of information security, unraveling the strategies and best practices needed to face the challenges of cyberspace. Join us on this journey towards a deep understanding of how to protect information in the digital age.
Protecting Your Personal Data
Personal data is any information that can be used to identify you and can exist both offline and online. Many people think that if they do not have any social media or online accounts, they do not have an online identity. This is not the case. If you use the web, you have an online identity. When choosing a username, it is important not to reveal any personal information.
- Do not use your full name or parts of your address or phone number.
- Do not use your email username.
- Do not use the same combination of username and password, especially for financial accounts.
- Do not choose a very strange username and then reuse it repeatedly, as it makes it easier to trace.
- Do not choose a username that gives clues about your passwords, such as a series of numbers or letters, the first part of a two-part phrase, or the department you work in, like IT.
- Choose a username that is appropriate for the type of account, i.e., business, social, or personal.
Your Data
Personal data describes any information about you, including your name, social security number, driver's license number, date and place of birth, and even photos or messages exchanged with family and friends. Cybercriminals can use this sensitive information to identify and impersonate you, infringing on your privacy and potentially causing severe damage to your reputation.
- Medical Records: Every time you visit the doctor, personal information about your physical and mental health and well-being is added to your electronic health records (EHR). Since most of these records are stored online, you should be aware of the medical information you share. These records extend beyond the doctor's office. For example, many fitness monitors collect large amounts of clinical data, such as heart rate, blood pressure, and blood sugar levels, which are transferred, stored, and displayed through the cloud. Therefore, consider these data part of your medical history.
- Educational Records: Contain information about your grades and academic achievements. However, these records can also include your contact information, attendance records, disciplinary reports, health records, and vaccination records, as well as any special education records, including individualized education programs.
- Employment and Financial Records: Employment data can be valuable to hackers if they can gather information about your previous employment or even your current performance evaluations. Your financial history may include information about your income and expenses. Your tax records may include paychecks, credit card statements, your credit rating, and your bank account details. If not adequately protected, all these data can compromise your privacy and allow cybercriminals to use your information for their benefit.
Personal Data vs. Business Data
Everything that travels over the network is vulnerable. Therefore, corporate IT security is crucial, as attackers will try to access the information under our control.
Personal Data is information that only interests you: photos, social networks, bank accounts, invoices, family information, among others. Ensure that the people who have access to these data are only those you want to have access.
Business Data are the data you have accessed since joining the company: clients, expenses, financial and tax information, metrics, statistics, results, among others. Companies ensure you do not share these data with others by asking you to sign an NDA (non-disclosure agreement).
| Personal | Organizational |
|---|---|
| Data and information that only interests me | Data that interests the organization |
| Social networks, photos | Client data |
| Bank accounts | Organizational structure |
| Invoices | Financial information |
| Family information | Metrics, statistics, and results |
| Tax information |
Where is Your Data?
The photos are no longer just on your device. In fact, they have ended up on servers located in different parts of the world, and people you do not even know now have access to your photos. This is just an example that reminds us that every time we collect or share personal data, we must consider our security.
Various laws protect privacy and data in your country. But do you know where your data are? After a consultation, the doctor will update your medical history. For billing purposes, this information may be shared with the insurance company. In such cases, your medical record, or part of it, is now available to the insurance company. Store loyalty cards may be a convenient way to save money on your purchases. However, the store is using this card to create a profile of your buying behavior, which it can then use to target you with special offers from its marketing partners.
Smart Devices
Unless you have chosen to receive printed statements (DINOSAUR), you probably access digital copies of bank statements through your bank's website. And when paying a bill, you most likely transferred the required funds through a mobile banking app. But besides allowing you to access your information, computing devices can now also generate information about you.
Wearable technologies, such as smartwatches and fitness trackers, collect your data for clinical research, patient health monitoring, and tracking fitness and well-being. As the global market for fitness trackers grows, so does the risk to your personal data. It may seem that the information available online is free. Social media companies generate most of their revenue by selling advertising based on customer data extracted through algorithms or formulas. Of course, these companies will argue that they are not "selling" customer data to their marketing partners.
CIA Triad: Confidentiality, Integrity, and Availability
A chain is only as strong as its weakest link. As our responsibility grows, so does the need for data security and privacy, confidentiality of our data and the impact that attackers or others accessing it can have.
Ensure that you, your colleagues, and your employees are not the weakest link in the chain. Employ strategies within your organization and daily life that help you protect information. Protect it yourself; do not expect others to do it for you, such as the IT department or the technology area. You can protect it yourself. Keep all your devices in sight, keep them locked or encrypted at all times.
Be careful with photos, as they contain much information that the next attacker might need. Make sure you are not the one exposing information that needs to be protected.
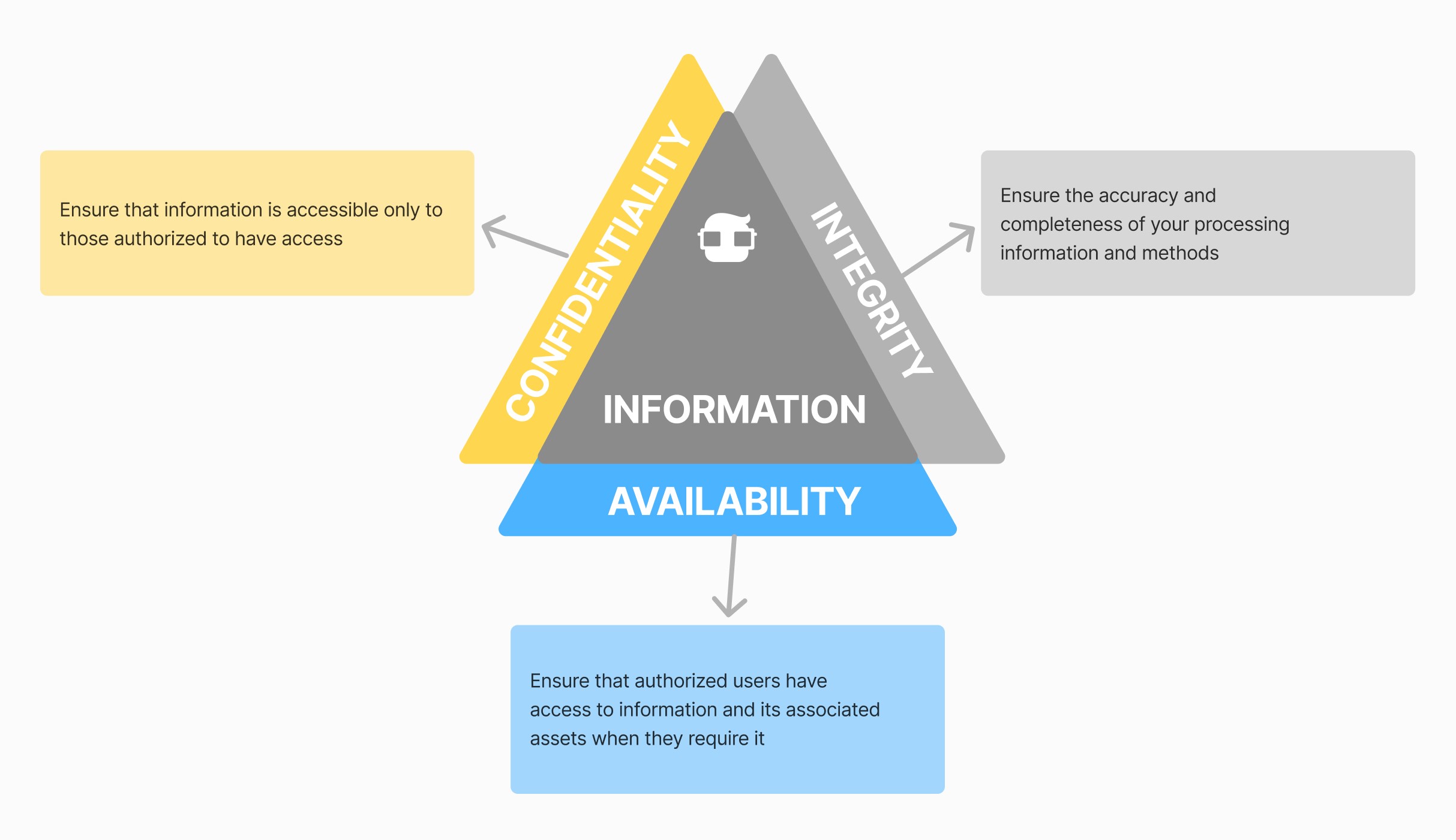
The CIA Triad consists of the following elements:
-
Confidentiality:
Example: An online purchase where you leave your card number, name, address, personal data, and others. The site where you make the purchase must ensure that the information you leave to make the purchase is confidential and that no one will have access to it, much less that it will be in plain, easily readable text.
-
Integrity:
Ensures that the information we store will remain intact throughout its life within the system and will not be modified without our authorization, even if we request changes, as the system keeps records of what has been changed. This integrity must ensure that the information remains intact and will be integrated into the system where it is managed and stored.
-
Availability:
Ensures that the information is always available to all authorized users. (Important: This information should only be available to authorized users).
This is why some sites ask you in a pop-up window if you allow them to use your personal data or not.
Everything we do in the organization or with the organization's information, if your role involves handling confidential information, the impact of losing that information or having an attacker capture it is much higher.
Organizational Data
Traditional Data: Usually generated and maintained by all organizations, large and small. It includes the following:
- Transactional Data, such as details related to buying and selling, production activities, and basic organizational operations, like any information used to make employment decisions.
- **
Intellectual Property**, such as patents, trademarks, and plans for new products, allows a company to gain an economic advantage over its competitors. This information is often considered a trade secret, and losing it can be disastrous for a company's future.
- Financial Data, such as income statements, balance sheets, and cash flow statements, provide information about the company's status.
Internet of Things (IoT) and Big Data: IoT is a vast network of physical objects, such as sensors, software, and other equipment. All these "things" are connected to the Internet, with the ability to collect and share data. And since storage options are expanding through the cloud and virtualization, it is no surprise that the emergence of IoT has led to exponential data growth, creating a new area of interest in technology and business called "Big Data."
The Cube
Let's expand on the CIA Triad concept. The McCumber Cube is a model framework created by John McCumber to help organizations establish and evaluate information security initiatives by considering all related factors that affect data security and privacy. This security model has three dimensions:
The Fundamental Principles to Protect Information Systems

As we have already seen, these principles refer to:
- Confidentiality is a set of rules that prevents sensitive information from being disclosed to unauthorized people, resources, and processes. The methods used to ensure confidentiality include data encryption, authentication, and access control.
- Integrity ensures that information or system processes are protected against intentional or accidental modifications. One way to ensure integrity is to use a hash function or checksum.
- Availability means that authorized users can access systems and data whenever and wherever needed, while those who do not meet the established conditions cannot. This can be achieved by maintaining equipment, performing hardware repairs, keeping operating systems and software updated, and creating backups.
Protecting Information in Each of Its Possible States
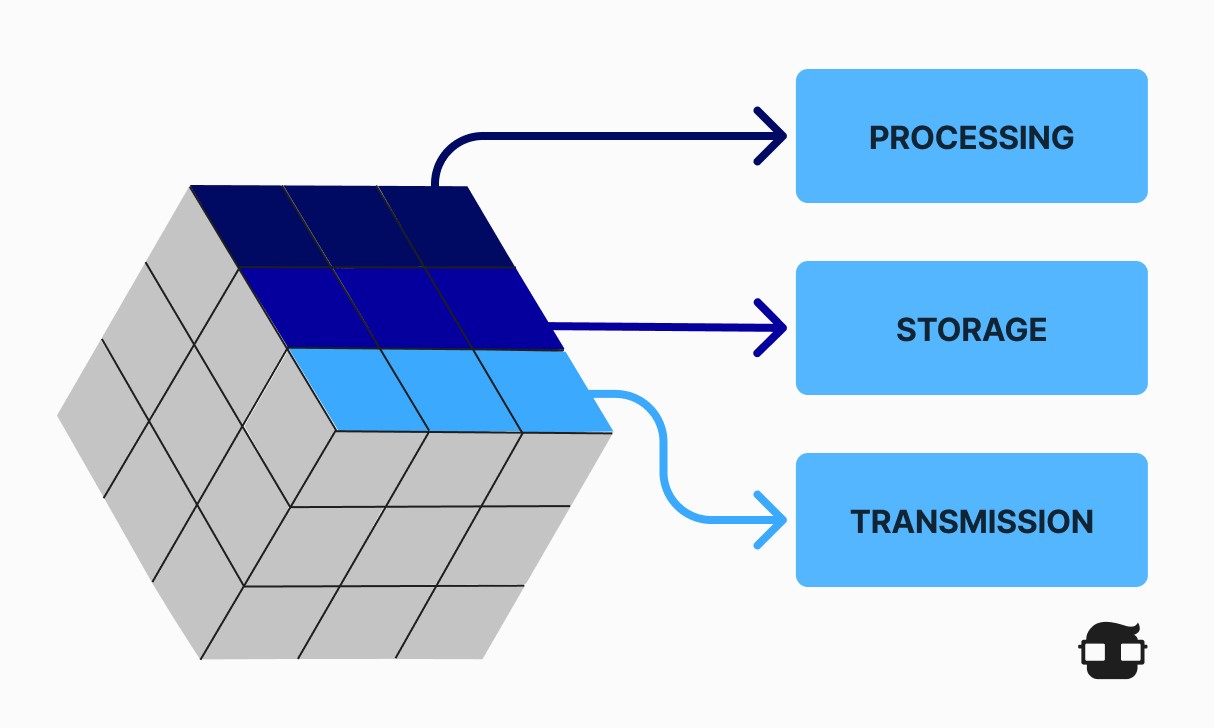
Security Measures Used to Protect Data
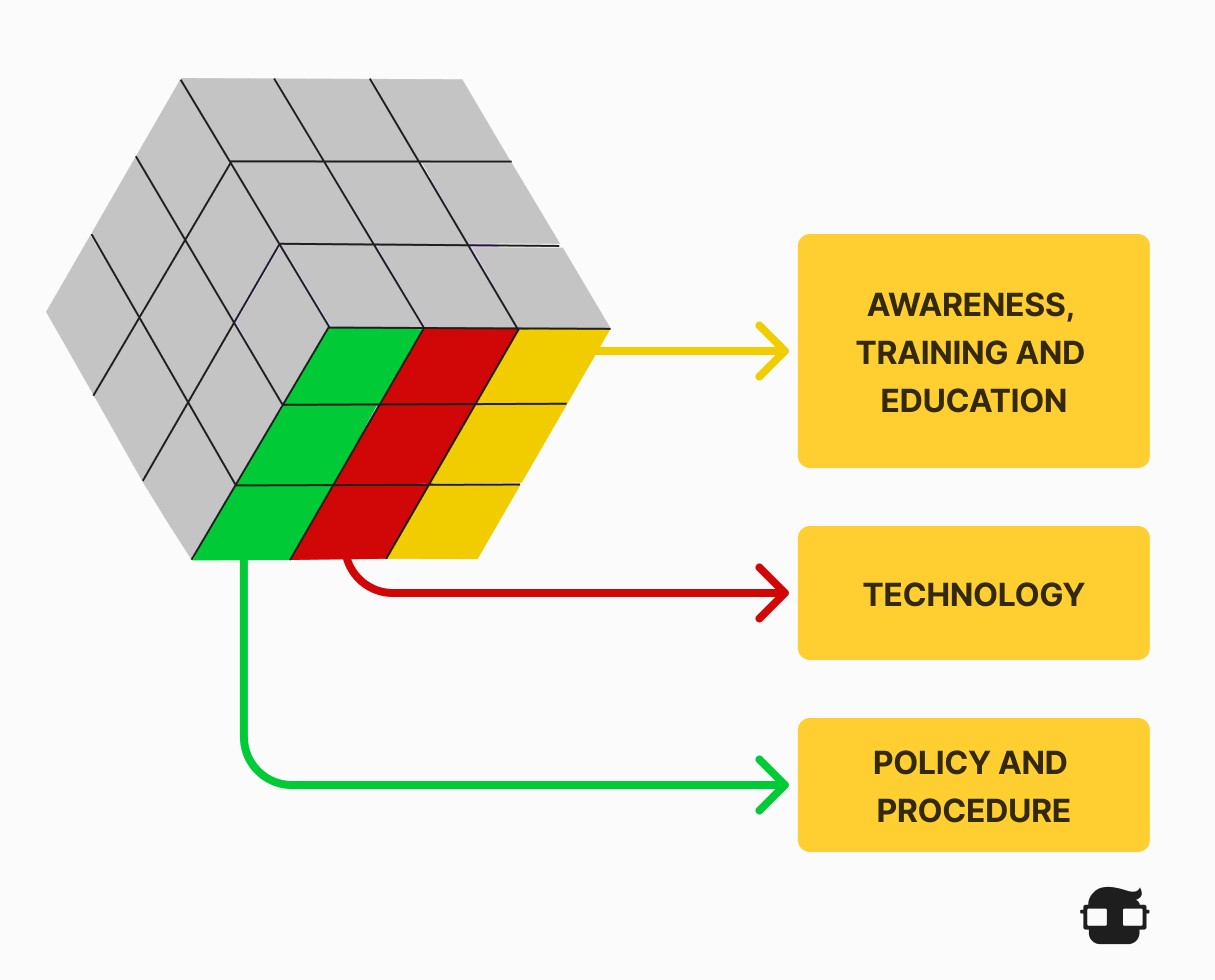
- Awareness, training, and education are the measures implemented by an organization to ensure that users are informed about potential security threats and the actions they can take to protect information systems.
- Technology refers to software (and hardware) solutions designed to protect information systems, such as firewalls, which continuously monitor your network for potential malicious incidents.
- Policy and Procedure refer to administrative controls that provide a foundation for how an organization implements information assurance, such as incident response plans and best practice guidelines.