Protecting Wireless Networks
Home wireless networks allow you to use your computer virtually from anywhere in the house, as well as connect with other computers on the network or access the Internet. However, if the wireless network is not secure, there are very important risks. For example, a hacker could:
- Intercept the data you send or receive.
- Access your shared files.
- Hijack your Internet connection and use all your bandwidth or download limit.
Internet Security Tips to Protect Your Wireless Network
Below are several simple steps you can take to protect your network and wireless routers:
- Avoid using the default password: It is very easy for a hacker to find out the default password from your wireless router’s manufacturer and use it to access the wireless network. Therefore, it is advisable to change your wireless router's administrator password. When setting the new password, try to choose a complex combination of numbers and letters, and try to avoid using a password that can be easily guessed.
⚠️ Don’t let your wireless device advertise its presence - disable the broadcast of the network identifier SSID (Service Set Identifier) to prevent the wireless device from announcing its presence to the world around you.
- Change the device's SSID name: As mentioned above, it is very easy for a hacker to find out the default SSID name of the device's manufacturer and use it to locate the wireless network. Change the default SSID name of the device and try to avoid using a name that can be easily guessed.
- Encrypt the data: In the connection settings, make sure to enable encryption. If the device supports WPA encryption, use it; otherwise, use WEP encryption.
- Protection against malware and Internet attacks: Make sure to install an effective antimalware program on all computers and other devices. To keep the antimalware protection up to date, select the automatic update option in the product.
Why is Wireless Security Important?
Wireless security is important because network vulnerabilities can expose unsecured data that can later be stolen and used against you. Even if your device has strong protection, other devices connected to your wireless network could be compromised if the network itself is not secure.
Your Internet router is not just where you can increase your home Wi-Fi connection strength. It is also a critical security hub. If the router has vulnerabilities, they could hijack your DNS settings, among other issues, and you might unknowingly visit fake or dangerous websites.
Public Wi-Fi networks (like those in restaurants and cafes) can also leave you exposed. Without strong security protocols, you might accidentally leave passwords and even online payment information available to someone on the same network looking for personal data.
Unless you have the best wireless security, any online device can be hacked. Fortunately, encryption standards have improved over the years to minimize vulnerabilities and neutralize threats. The best Wi-Fi security protocol will prevent your router from being attacked and help you browse safely on public Wi-Fi. Let's take a look at the different types of Wi-Fi security that have been implemented over the years.
Types of Wi-Fi Security Protocols
The most common wireless security protocol types today are WEP, WPA, and WPA2. Each protocol uses a different type of encryption to enhance network security. The most recent protocols, including the latest WPA3, have proven to be very robust, making it more difficult for hackers to implement workarounds.
Wired Equivalent Privacy (WEP)
Wired Equivalent Privacy (WEP) was the standard form of encryption, but it is no longer secure because computing power has improved and hackers can now easily crack it. WEP security is encrypted with a static key, one of the main reasons it is no longer considered secure.
WEP, introduced in 1997, uses a single key to secure an entire network. If one user is compromised, everyone on the network is. When WEP security was introduced, the 64 or 128-bit string was difficult to crack, creating a formidable wall between a network of users and hackers trying to intercept wireless signals.
Now, performing the necessary calculations to crack a WEP key is a trivial matter for even a home computer. The WEP security protocol was retired in 2004, so systems still using it should be updated.
Pros:
- Most devices recognize WEP, which means it was easy to set up and use.
- Its goal was to match the security advantages of wired Internet connections.
- When introduced, the encryption algorithm was complex enough to keep unknown users away.
- WEP protected against man-in-the-middle attacks.
Cons:
- It used a static encryption key that had to be manually changed and updated on each individual machine to ensure the security benefits of later protocols.
- Part of the key was transmitted as easily decipherable plain text.
- Countless security holes have been discovered over the years.
Wi-Fi Protected Access (WPA)
WPA (Wi-Fi Protected Access) security was designed to address many issues that arose with WEP. WPA became the standard in 2003 and encrypts the network access key dynamically, changing it regularly with TKIP (Temporal Key Integrity Protocol). This way, hackers can no longer crack the key by collecting data transmitted over a long period of time.
TKIP created a dynamic security environment, but it still wasn't enough. Security experts quickly discovered that TKIP could be cracked even with small amounts of data.
As a result, cryptographers worldwide were asked for encryption (or encryption algorithms) to replace WEP and WPA's RC4 encryption, and the Belgian-made AES encryption proved to be the most secure during the competitive selection process. AES found widespread adoption with WPA's successor, WPA2, which we will discuss in the next section.
Pros:
- Introduced TKIP, or dynamic key encryption, which regularly changes the network access key.
- All devices on the network recognize the new key when it is generated.
- Increased the complexity of security keys and their authentication.
Cons:
- TKIP has proven to be vulnerable and can be easily hacked.
- The complexity of the algorithm can be overcome with modern processing power.
- Unless users and network administrators created strong passwords, the data was vulnerable.
- When comparing WPA to WEP, WPA's security advantages were significant, but WPA's flaws became apparent quickly.
Wi-Fi Protected Access II (WPA2)
The WPA2 security protocol increased the complexity of its predecessor (WPA) and has been the network security standard for over a decade. It uses AES encryption, an encryption process that even an advanced computer would need billions of years to crack.
But WPA2 also has security flaws. A KRACK attack can gain access during the communication establishment when a network authenticates a device's connection, leaving the victim's passwords and other data vulnerable. To carry out such an attack, the hacker must be very close to the network, which is not ideal even for the best hackers.
The significant security differences between WPA and WPA2 have made the WPA2 protocol last longer than any previous security protocol.
Pros:
- Retains the same benefits introduced with WPA.
- Usually uses AES encryption, an extremely robust encryption.
- Requires longer passwords, which adds additional security.
Cons:
- Requires a greater amount of processing power (now insignificant with current technology).
- Can be vulnerable to man-in-the-middle attacks.
- After more than a decade since its introduction, a flaw was finally discovered.
And the WPA3 Protocol?
WPA3 was introduced in 2018 and became a standard security protocol in 2020, but widespread adoption may take time. Most homes and businesses still use WPA2, and WPA3-compatible hardware can be expensive. With WPA3, encryption between the user's device and the network is specific and individualized, and users won't even have to enter a password.
With WPA2, a device and its data can be compromised once a hacker breaks the network encryption. That will no longer be possible with WPA3 due to the added layer of individualized encryption.
WPA3 also addresses the WPA2 security flaw that allows KRACK attacks. And the encryption algorithm is much more complex, so much so that modern computers would need billions of years of calculations to enter a single WPA3-protected network.
- WPA vs. WPA2
Let's summarize the differences between WPA and WPA2.
| Criterion | WPA | WPA2 |
|---|---|---|
| Introduction date | 2003 | 2004 |
| Best available encryption method | TKIP, an imperfect system that can be cracked | AES, the most secure encryption widely available |
| Password length | Minimum length is very short, which compromises security | Minimum length is long, which enhances security |
| Options for home and business | Only for home | Business option |
| Processing power required | Minimal | More than WPA, but insignificant by current standards |
| Security flaw discovery date | 2008 | 2018 |
Currently, WPA2 remains the standard protocol for Wi-Fi security, primarily due to its strong AES encryption method.
- WEP vs. WPA and WPA2
WPA2 is the best available security protocol today, and we will all continue to use WPA2 passwords at homes and cafes for several years. WPA2 uses a dynamic network access key and multiple layers of protection for any network it protects. Meanwhile, the old WEP standard has a static key that is easily crackable.
Of all the types of Wi-Fi security, WPA2 takes the longest to crack. And this vulnerability is still only theoretical: it has not yet been seen in the real world. WEP and WPA protocols have been shown
to be crackable within minutes, so neither homes nor businesses should use them.
- WEP, WPA, or WPA2, Which Wi-Fi Security Protocol is Best for My Router?
The best Wi-Fi security option for your router is WPA2-AES. You may see WPA2-TKIP as an option, but it is not as secure. However, WPA2-TKIP is the second most secure, followed by WPA and WEP.
WPA3 will soon become the most secure option once widely adopted, and you should switch to that protocol when it becomes available.
Here are the security standards ranked from best to worst. Follow the proper security recommendations, and your home or business Wi-Fi will be as secure as possible.
- WPA2 + AES
- WPA2 + TKIP
- WPA + AES
- WPA + AES/TKIP (TKIP is used as a backup method)
- WPA + TKIP
- WEP
- Open network
Even some security is better than none, so make sure to implement one of these options, even if the best is not available to you. Use a long and complex password and change it regularly to keep a WEP or WPA connection a little more secure than it would otherwise be.
👉 If you want to buy a new router or connect to the Internet with a new provider, check if you can get a WPA3-certified router. You don't need to worry about transition periods or compatibility issues: it will be all set to use the most capable and secure option once WPA3 is available for your network.
Hopefully, that invaluable little box will do what it should, and router virus removal will become a thing of the past. And maybe none of us will ever have to worry about fixing a Wi-Fi that doesn't work.
How Can I Find My Current Wi-Fi Security Protocol?
Here is how to find the Wi-Fi security protocol you are using:
- Click on the Windows Start menu and select Settings (the gear icon).
- Select Network & Internet.
- Choose Wi-Fi from the left panel.
- Click on the name of the wireless network you are connected to.
- Next to Security type, you will see the wireless network protocol you are using.
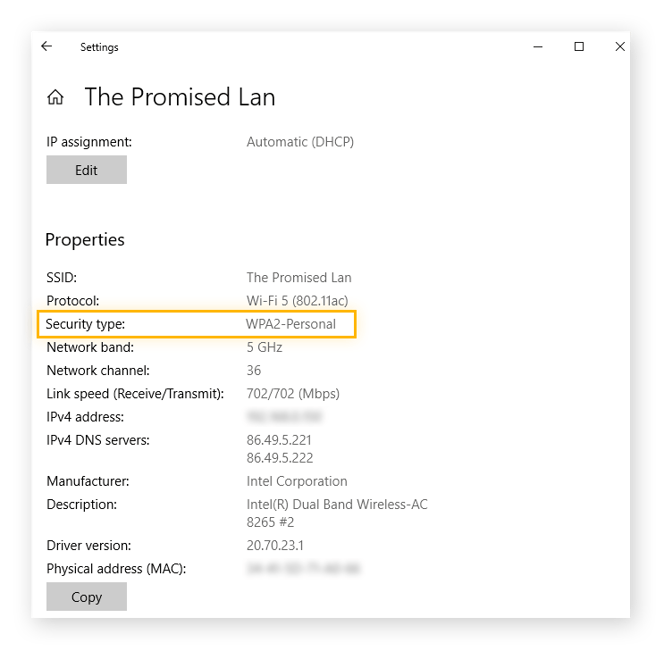
If you are using WPA2 versus WPA3 but want to switch to WPA3, you must first ensure that the Protocol field in your Wi-Fi network settings says Wi-Fi 6.
Wireless Security Vulnerabilities
Common Risks and Threats
Wi-Fi networks, while providing great convenience, are not without risks and threats that could compromise our online security and become insecure. Among the most common threats lurking in the world of wireless networks is unauthorized access. This means that intruders can take advantage of unprotected Wi-Fi networks or weak passwords to connect without permission, which could result in bandwidth theft, data interception, and the exploitation of vulnerabilities in connected devices. But this does not mean that the Wi-Fi technology is not secure.
In addition, Wi-Fi phishing has become an increasingly sophisticated tactic used by cybercriminals. By creating fake networks that mimic legitimate network names, attackers trick users into connecting to them and disclosing sensitive information such as passwords and banking details.
Brute force attacks are also a concern, as attackers attempt to guess weak passwords by repeatedly trying combinations to gain unauthorized access to the network. These threats can have serious consequences, from losing personal data to hijacking online accounts, so it's essential to be aware of the dangers lurking in the world of Wi-Fi and take steps to protect yourself against them so that our Wi-Fi networks are as secure as possible.
Another common type of attack is the " deauthentication" type, which is based on sending "deauthentication" frames to valid network users to try to disconnect them from an access point and try to capture messages with the AP to obtain the network access key. However, when we talk about insecure Wi-Fi, we must consider that many new standards add new security features, as do the different manufacturers.
The 802.11W standard is one of the new forms of protection for this type of attack, making each new standard Wi-Fi technology less insecure.
Vulnerabilities in Wi-Fi Networks
Vulnerabilities in Wi-Fi networks are small invisible sections in wireless connectivity that cybercriminals can exploit. One of the most notorious and dangerous vulnerabilities is using weak or predictable passwords. Many users still use simple passwords like "123456" or "password" to protect their Wi-Fi networks, which makes unauthorized access very easy. In these particular cases, it is the user who defines whether their Wi-Fi network is insecure.
Another point of vulnerability is the use of the WEP (Wired Equivalent Privacy) security protocol, which has become obsolete and is susceptible to relatively simple decryption attacks. It is no longer common to see this type of security protocol in production Wi-Fi networks, as it would be an insecure Wi-Fi network.
Wi-Fi networks can also be vulnerable due to incorrect Access point configurations. This includes using default configurations known to attackers, such as network names (SSID) or pre-set passwords that have not been changed. In addition, failing to update the Access point firmware can leave the door open to known vulnerabilities that manufacturers fix in updates.
📖 These vulnerabilities are weak points that cybercriminals can exploit to compromise your Wi-Fi network's security. To protect yourself properly, it is essential to recognize these vulnerabilities and take steps to correct them, such as using strong and unique passwords, upgrading the security protocol to WPA3, and properly configuring the Access point or router to minimize risks. With a proactive approach to security, you can strengthen the integrity of your Wi-Fi network and ensure a safer browsing experience. If you do not apply measures to your wireless network, it could be an insecure Wi-Fi network.
Tips to Protect Your Wireless Network
The security of your Wi-Fi network is a crucial priority to protect your data and privacy in today's connected world. Fortunately, there are a number of practical tips you can follow to strengthen your wireless network's security and eliminate an insecure Wi-Fi network. First, choosing a secure and unique password is essential. Avoid obvious or predictable passwords and opt for combinations of letters, numbers, and special characters that are difficult to guess. Changing your password regularly is also a good security practice.
Updating your Access point's firmware according to the hardware manufacturer is another important step. Manufacturers often release updates to address vulnerabilities and improve security, so keeping your Access point or router up to date is essential to avoid having an insecure Wi-Fi network.
Enabling WPA3 encryption (or WPA2 if your device is not compatible) is key to protecting communication between your device and the router. WPA3 offers a higher level of security for your Wi-Fi network and encryption than its predecessors. You can also increase security by configuring MAC address filters, allowing only authorized devices to connect to your network. Remember to change your network's default name (SSID) and disable its broadcast. This makes it more difficult for intruders to identify your network.
Finally, consider the possibility of setting up a separate guest network for visitors with limited access to your main resources. By following these tips, you can significantly strengthen the security of your Wi-Fi network and reduce the risk of attacks and unauthorized access, ensuring a safer and more reliable browsing experience for you and your connected devices. Using VLANs is a common recommendation for guest networks and Layer 2 isolation (if your equipment supports it, it is also important).
Standards like 802.11w make Wi-Fi networks more secure, and as technology continues to grow, we will have more effective and secure Wi-Fi networks.
Security Measures for Wireless Networks
Wi-Fi networks have carved out an important place in our homes and businesses. They have only been with us for a few years, but in that time, they have become almost indispensable in many everyday activities that go beyond Internet connectivity, as they also allow us to manage all kinds of gadgets and devices remotely.
Despite their growing importance, many users pay little attention to the configuration of their wireless network. They simply plug in the carrier's router and start browsing. Generally, there should be no major problems, but if we do not take certain precautions, an intruder may enter our network and cause us more than a headache.
Usually, they will not be spies or evil hackers like those seen in movies who try by all means to take advantage of our Wi-Fi to commit crimes, although there are some. It is common for a neighbor to try to sneak into our network to save on connection costs, making us initially responsible for the websites they visit.
📖 How can we avoid these unwanted intrusions into our Wi-Fi? Well, although total security does not exist (for that, we would have to turn off the network, of course), we can follow a series of simple and slightly more complex tips and tricks, which we will explain below.
Secure Access to Your Router
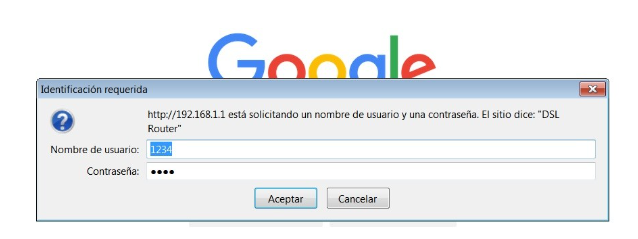
First, we must ensure that no one outside of us can access the router to control our Wi-Fi. Otherwise, everything we do will be useless, as they can enter and reverse it or even deny us access to our own network.
Therefore, the first step is to update the router's firmware to the latest version available to fix possible vulnerabilities that have been detected, a process that will depend
on each specific brand and model, and then start by changing the default access password that is usually provided by the manufacturer or carrier.
Do not let the door to your home connection center open with the classic 1234/1234 or admin/admin. Find a username and a personalized password that you can remember well or leave noted in a place you know in case you forget them. Changing the router's default IP address can also be useful. It is usually 192.168.1.1, the first digits every user eager to hack your Wi-Fi will type into their browser. Simply changing the last digit can delay or deter less experienced hackers or that neighbor who wants to take advantage of your connection.
Change the SSID Name
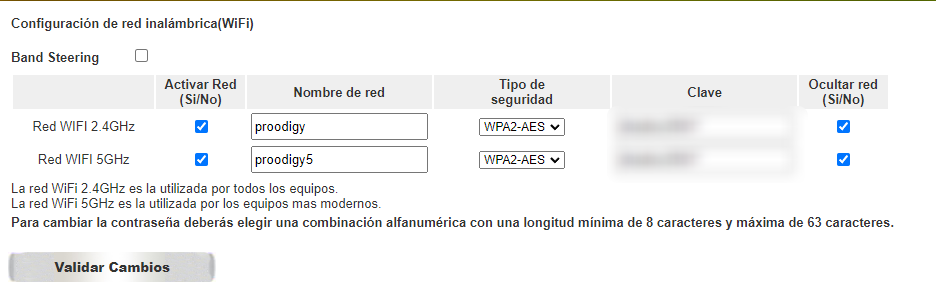
The SSID (Service Set Identifier) or wireless network identifier is used precisely for that, to identify it among many others. It is common for it to be provided by the carrier that provides us with the router, sometimes showing more information than it should about the type of router we have and its potential vulnerabilities.
Ideally, we should use a name that is easy to remember or that we find some personal connection to but that does not directly reference us or our home. We can be as creative as we want, even hide the SSID altogether if the router allows it or create multiple ones with different guest access permissions.
But never use your name, nickname, physical address (Wi-Fi on the 4th B), or email address (yes, it seems absurd, but it happens), as we would be giving unnecessary clues about who owns the network.
Choose the Best Encryption System and Change the Default Password
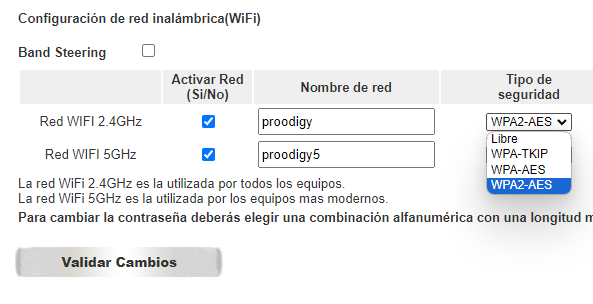
An essential aspect of wireless network security is the encryption of the data that will be transmitted through them. There are mainly three different systems or protocols that can be found in most modern routers: WEP, WPA, and WPA2.
WEP has become obsolete. Whenever possible, choose the WPA encryption system or better yet WPA2 for greater security.
WEP is the most basic of the three, providing level 2 encryption and has become obsolete as the protection can be broken with a computer or medium-power device in a few minutes. The next option is WPA, which was born just as a solution to WEP's most obvious vulnerabilities. Its acronym means something like "Wi-Fi Protected Access," and it is a much more secure system against password attacks, not being as limited in the number of characters we can enter.
Finally, we have WPA2, the evolution of WPA that offers the highest level of protection of the three. Whenever possible, we should choose it, although we must be careful that all devices on the network support it (older ones may not be compatible), or they will not be able to communicate.
Of course, regardless of which we choose, we must set a password complex enough that no one can or at least find it easy to assault it by brute force but that is relatively easy to remember, especially if we want to use new devices frequently that will require the password to be entered the first time they connect. It is also good to change this password from time to time to prevent potential intrusions with brute force attacks.
Use MAC Filtering
Another security measure that can be useful is the so-called MAC filtering (it is not about not letting Apple devices connect, no). MAC addresses or also called physical addresses are assigned to each network card directly in its hardware and uniquely identify it from the rest. It is somewhat like an IP address but at a lower level and is only used within the same subnet.
MAC filtering allows you to create a kind of list of allowed network devices. It consists of 48 bits and is represented in 6 groups of hexadecimal numbers separated by colons or hyphens. It looks like this: 01:23:45:67:89:AB or expressed as 01-23-45-67-89-AB.
Where can I find it? It depends on the device and the operating system we use. On some gadgets, we can even see it on a sticker or the device's box. This article provides several examples of where and how to find it. MAC filtering will consist of creating a kind of list of network devices allowed to connect to our Wi-Fi. To do this, we must enter the router's corresponding option and enter the addresses we want to authorize on our network.
Depending on the model, we can also create blacklists of blocked devices, thus preventing access to devices we know for sure are intruders or leeches on our Wi-Fi. This article provides more details on how to properly perform this MAC filtering with a specific case.
Reduce Allowed IP Address Ranges
If we always have the same devices connected to the network, we can disable the DHCP service (Dynamic Host Configuration Protocol) automatic operation in the router, which assigns IP addresses to each device connected to the network.
This will force us to configure the values manually on all the devices we have at home, but it can add an extra layer of security. We can also play with the range of allowed IP addresses and restrict it to the values we want, avoiding leaving multiple addresses available.
It is very easy to do. Just look in the router for the option within the LAN configuration that says something like Start IP Address/End IP Address and specify the desired values (for example, from 192.168.1.33 to 192.168.1.35, which would allow us to connect three devices to the network). If the router also allows us to change the validity time of this assignment, we can also indicate a very high figure, leaving none available for an intruder, as there will be no free slots.
Limit the Antenna Emission Power
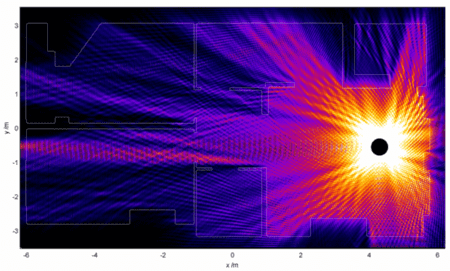
Simulation of the Radiated Power by a WiFi Signal
It may seem obvious, but it is the most effective method to prevent intrusion or unauthorized use of your wireless network. If the signal does not reach, it is difficult for someone to locate your network and even more so to connect to it. Most routers allow you to manage the power emitted by the antennas and thus manage the network's coverage radius approximately. Usually, we find some option that allows us to vary the percentage of signal level or transmitted power.
Here we must try to lower the intensity so that we can still connect to the network inside the house, but so that the power drops significantly outside. We can check it by simply moving around the house and its surroundings with a mobile phone to see what Wi-Fi coverage we have.
How much do I need to reduce it? As much as you can without harming yourself or losing connection. It may also be helpful to orient the router's antennas, if we can do so, towards the interior of the house to provide maximum power inside and minimize it as much as possible to the outside, and if we are somewhat paranoid, use some metallic reflector to modify the direction of the energy beam or even use some type of anti-electromagnetic radiation paint on some walls where we don't want the Wi-Fi signal to exit.
In Summary
Although total security does not exist, following the simple tips mentioned above, you will be able to maintain a good level of privacy on your wireless network, which will surely deter most neighbors and potential spies. What steps do you need to follow? Here is a summary:
- Secure access to your router by changing default passwords and IP addresses.
- Change the SSID name or hide it altogether.
- Choose WPA or better yet WPA2 encryption system and a long alphanumeric password.
- Use MAC filtering and create a list of allowed devices on your network.
- Reduce allowed IP address ranges on your local network.
- Limit the power emission of antennas to the exterior of your home.