Windows CMD Commands for Remote Hacking
Many new hackers come from Windows environments but rarely (if ever) utilize its built-in command line tools. As a hacker, you will often need to control the target system using only Windows commands without relying on a GUI.
While tools like Metasploit's Meterpreter offer extensive capabilities, they are not always available. Some exploits only grant a CMD shell on the target Windows system. In these cases, understanding how to control the system strictly through the command prompt is essential.
This lesson demonstrates essential Windows CMD commands by executing them from a remote Kali system on the target.
1. File System Navigation
Purpose:
Commands:
-
1cd \ -
cd ..
Move up one directory level.1cd .. -
dir
List the contents of the current directory.1dir -
md <directory>
Create a new directory (equivalent tomkdirin Linux).1md newdirectory
After creating a new directory, running dir will display the newly created directory.
2. File Management
Purpose:
Manage files by creating, viewing, and deleting them within the file system.
Commands:
-
del <filename>
Delete a specified file.1del confidential.txt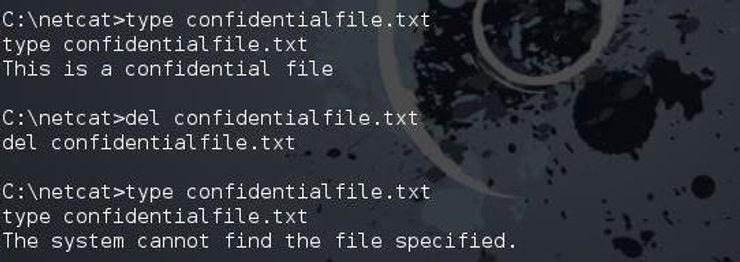
After deletion, attempting to display the file's contents will result in:
The system cannot find the file specified. -
type <filename>
Display the contents of a specified file (similar tocatin Linux).1type confidential.txt -
copy <source> <destination>(Optional Addition)
Copy files from one location to another.1copy file1.txt D:\backup\file1.txt -
move <source> <destination>(Optional Addition)
Move or rename files.1move file1.txt D:\documents\
3. Process Management
Purpose:
Monitor and control running processes on the target system to manage system behavior or disrupt services.
Commands:
-
tasklist
List all running processes.1tasklist
-
tasklist | findstr <process_name>
Filter the list of processes to find a specific one (similar togrepin Linux).1tasklist | findstr explorer
-
taskkill /PID <ProcessID> /F
Terminate a process using its Process ID (PID) with force (/F).1taskkill /PID 1532 /F
4. Networking
Purpose:
Commands:
-
ipconfig
Display the network configuration of the system (similar toifconfigin Linux).1ipconfig
-
netstat
Show active network connections and listening ports.1netstat
-
ping <address>(Optional Addition)
Test the reachability of a host on the network.1ping www.google.com -
tracert <address>(Optional Addition)
Trace the route packets take to reach a network host.1tracert www.google.com
5. User and Account Management
Purpose:
View and manage user accounts on the target system, which can be crucial for privilege escalation or lateral movement.
Commands:
-
net user
Display a list of user accounts on the system.1net user
-
net user <username>(Optional Addition)
Display detailed information about a specific user account.1net user administrator -
whoami(Optional Addition)
Display the current logged-in user.1whoami
6. Executing Applications
Purpose:
Run applications on the target system to perform tasks or deploy further payloads.
Commands:
-
iexplore <URL>
Launch Internet Explorer and navigate to a specified URL.1iexplore www.google.comThis command opens Internet Explorer on the target system and navigates to google.com, useful for deploying payloads via malicious links or directing the target to a controlled web server.
-
start <application>(Optional Addition)
Start a specified application (e.g., Notepad).1start notepad.exe
7. System Information and Diagnostics (Optional Section)
Purpose:
Gather detailed information about the system's hardware and software configuration.
Commands:
-
systeminfo
Display detailed configuration information about the computer and its operating system.1systeminfo -
wmic(Windows Management Instrumentation Command-line)
Interact with Windows Management Instrumentation to query system details.1wmic cpu get name, maxclockspeed, currentclockspeed
8. Privilege Escalation (Optional Section)
Purpose:
Gain higher-level permissions on the target system to perform restricted actions.
Commands:
-
runas /user:<username> <command>
Run a command with different user credentials.1runas /user:Administrator cmd.exe -
whoami /groups
List the groups the current user belongs to, helping identify privilege escalation paths.1whoami /groups
9. Ethical Considerations
Understanding and utilizing these commands comes with significant ethical responsibilities. Always ensure you have explicit permission to perform any penetration testing or system control activities. Unauthorized access or control of systems is illegal and unethical. Use these skills to improve security and protect systems, not to exploit vulnerabilities unlawfully.
Additional Recommendations
-
Correct Command Syntax:
Ensure all command examples are accurate. For instance:- Replace
from <filename>withdel <filename>. - Correct
tareakilltotaskkill. - Fix
findtrtofindstrand ensure the example uses the correct syntax (tasklist | findstr explorer).
- Replace
-
Advanced Commands:
For more seasoned learners, introduce advanced CMD commands such as:regfor registry manipulation.schtasksfor managing scheduled tasks.
-
Hands-On Exercises:
Incorporate practical exercises at the end of each section to reinforce learning. For example:- Navigate through directories and create/delete folders.
- List and terminate specific processes.
- Execute a browser to visit a controlled web server.
-
Visual Enhancements:
Ensure all screenshots (Buffer 21,Buffer 22, etc.) are clearly labeled and correspond accurately to the commands being demonstrated.
Use Case: Enumerating System Information and Managing Processes for Stealthy Access
Objective:
To gain comprehensive insights into the target system's configuration and running processes, identify potential targets for privilege escalation, and terminate security-related processes to maintain stealthy access.
Scenario:
You have successfully established a remote CMD shell on a target Windows system. Your goal is to gather system information, enumerate user accounts, identify running security processes, and terminate those processes to prevent detection and maintain persistent access.
Step-by-Step Guide:
1. Gather System Information
Purpose:
Understand the target system's configuration, including the operating system version, installed updates, and hardware details. This information is crucial for identifying vulnerabilities and planning further actions.
Commands:
-
systeminfo
Displays detailed configuration information about the computer and its operating system.1systeminfo -
wmic cpu get name, maxclockspeed, currentclockspeed
Retrieves information about the CPU, including its name and clock speeds.1wmic cpu get name, maxclockspeed, currentclockspeed
Explanation:
By executing these commands, you obtain a comprehensive overview of the system's hardware and software environment, which is essential for identifying potential vulnerabilities and understanding the system's capabilities.
2. Enumerate User Accounts
Purpose:
Identify all user accounts on the target system to find potential targets for privilege escalation or lateral movement.
Commands:
-
net user
Displays a list of user accounts on the system.1net user -
whoami
Displays the current logged-in user.1whoami1whoami /groups
Explanation:
Listing all user accounts helps in identifying administrative accounts or users with elevated privileges. The whoami command reveals the current user's identity and group memberships, which is vital for assessing the level of access and potential escalation paths.
3. Identify and Terminate Security Processes
Purpose:
Locate and terminate security-related processes (e.g., antivirus software) to reduce the chances of detection and interfere with the system's defense mechanisms.
Commands:
-
tasklist
Lists all running processes.1tasklist -
tasklist | findstr "antivirus"
Filters the list to find processes related to antivirus software.1tasklist | findstr "antivirus"1tasklist | findstr "explorer" -
taskkill /PID <ProcessID> /F
Terminates a specific process using its Process ID (PID) with force.1taskkill /PID 1532 /F
Explanation:
By identifying and terminating security processes, you can minimize the risk of your activities being detected by antivirus or other security software. This step is crucial for maintaining stealthy access and preventing the system from initiating countermeasures.
4. Navigate the File System and Manage Files
Purpose:
Organize your tools and payloads within the target system to ensure easy access and execution during future sessions.
Commands:
-
md C:\Windows\Temp\Payloads
Creates a new directory named "Payloads" within the Temp folder.1md C:\Windows\Temp\Payloads -
copy payload.exe C:\Windows\Temp\Payloads\
Copies the payload executable to the newly created directory.1copy payload.exe C:\Windows\Temp\Payloads\
Explanation:
Creating a dedicated directory for your tools ensures that they are organized and easily accessible. Copying payloads to this directory prepares the system for executing further commands or establishing persistent access.
5. Execute Applications to Maintain Access
Purpose:
Run your payload or backdoor to establish a persistent connection or execute malicious activities on the target system.
Commands:
-
start C:\Windows\Temp\Payloads\payload.exe
Launches the payload executable.1start C:\Windows\Temp\Payloads\payload.exe -
tasklist | findstr "payload"
Verifies that the payload is running.1tasklist | findstr "payload"
Explanation:
Executing your payload is essential for establishing a backdoor or maintaining access to the target system. Verifying that the payload is running ensures that your actions have been successful and that you can rely on this access for future operations.
6. Cleanup and Cover Tracks
Purpose:
Remove any traces of your activities to avoid detection and maintain long-term access without raising alarms.
Commands:
-
del C:\Windows\Temp\Payloads\payload.exe
Deletes the payload executable after execution.1del C:\Windows\Temp\Payloads\payload.exe -
rmdir C:\Windows\Temp\Payloads
Removes the Payloads directory.1rmdir C:\Windows\Temp\Payloads
Explanation:
Cleaning up by deleting your payloads and removing directories helps in erasing evidence of your presence on the system. This step is crucial for maintaining stealth and reducing the chances of your activities being discovered during system audits or security scans.
Summary of Commands Used:
- File System Navigation & Management:
mdcopydelrmdir
- System Information:
systeminfowmic
- User and Account Management:
net userwhoamiwhoami /groups
- Process Management:
tasklistfindstrtaskkillstart