Pentesting Phases Explained
The phases of pentesting (penetration testing) are structured sets of steps designed to simulate real attacks on a system or network in order to identify and exploit vulnerabilities. These phases provide a methodical approach to assessing the security of an environment. Below are the typical phases of pentesting:
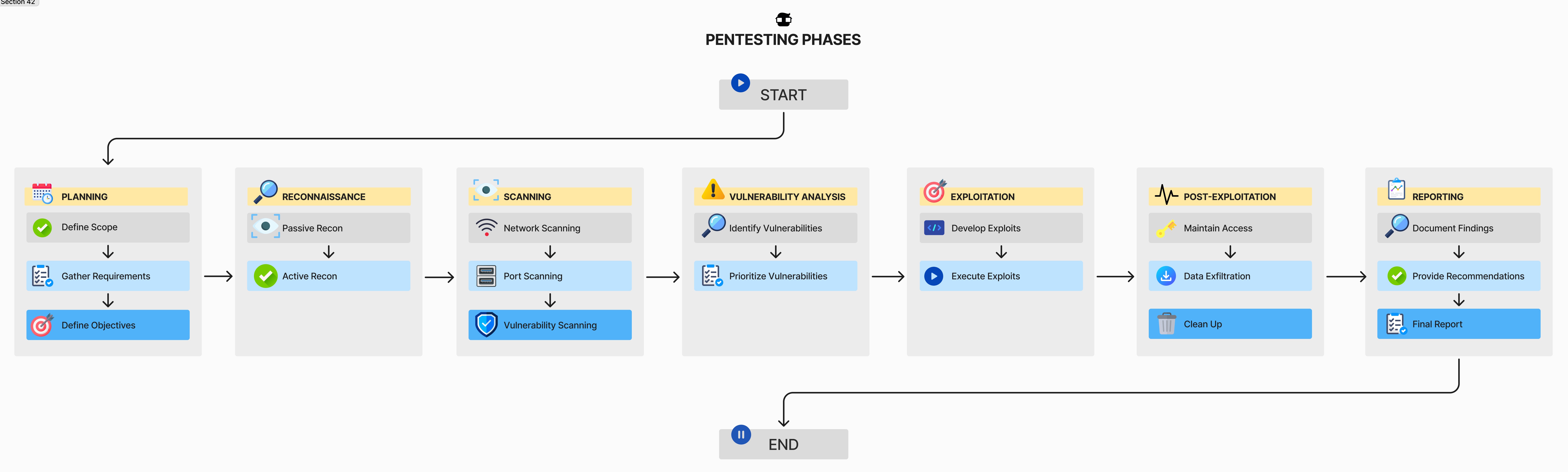
1. Planning
Objective: Establish the foundations and scope of the penetration testing project. This phase ensures that all involved parties clearly understand the objectives, scope, required resources, and limitations of the pentesting. Specific goals are identified, requirements are gathered, and strategies and methodologies to be employed are determined.
Activities:
- Determine the networks, systems, and applications to be evaluated.
- Identify areas excluded from the pentesting.
- Establish specific pentesting objectives, such as finding critical vulnerabilities, assessing the security of specific applications, etc.
- Obtain general information about the IT infrastructure.
- Gather data on network configurations, types of operating systems, applications used, etc.
2. Reconnaissance
Objective: Gather information about the target to prepare for later phases of pentesting.
Activities:
- Passive Reconnaissance: Obtain information without directly interacting with the target system, using public sources like WHOIS, DNS records, social networks, and search engines.
- Active Reconnaissance: Interact directly with the target system to gather information, such as port scanning, service identification, and network traffic analysis.
3. Scanning and Enumeration
Objective: Identify open ports, running services, and gather more details about the target system.
Activities:
- Port Scanning: Use tools like Nmap to identify open ports and associated services.
- Service Enumeration: Gather detailed information about running services, software versions, and specific configurations.
- Vulnerability Detection: Utilize vulnerability scanning tools to identify potential weaknesses in detected services and applications.
4. Exploitation
Objective: Attempt to exploit identified vulnerabilities to gain unauthorized access or compromise the target system.
Activities:
- Vulnerability Exploitation: Use known exploits and develop customized techniques to leverage detected vulnerabilities.
- Access Obtaining: Access systems and data without authorization.
- Privilege Escalation: Attempt to gain higher privileges within the compromised system.
5. Post-Exploitation
Objective: Assess the impact of exploitation and determine the scope of system compromise.
Activities:
- Maintain Access: Establish methods to maintain access to the compromised system (backdoors, persistence).
- Lateral Movement: Attempt to move through the network to compromise other systems.
- Information Extraction: Gather sensitive data and assess the potential impact of exploitation.
6. Analysis and Reporting
Objective: Document pentesting findings and provide recommendations to mitigate vulnerabilities.
Activities:
- Results Analysis: Evaluate data collected during previous phases to identify patterns and determine the severity of exploited vulnerabilities.
- Report Compilation: Create a detailed report describing identified vulnerabilities, exploitation methods used, potential impact, and mitigation recommendations.
- Client Review: Present findings and discuss recommendations with the security team and other stakeholders.
7. Remediation and Validation
Objective: Correct identified vulnerabilities and verify that implemented solutions are effective.
Activities:
- Patch Application and Configurations: Implement solutions to correct identified vulnerabilities.
- Remediation Validation: Conduct additional testing to ensure vulnerabilities have been properly mitigated.
Conclusion
The phases of pentesting provide a structured framework for evaluating the security of a system or network by simulating real attacks. These phases include reconnaissance, scanning and enumeration, exploitation, post-exploitation, analysis and reporting, and remediation and validation. By following this methodical approach, pentesters can effectively identify and mitigate vulnerabilities, thereby improving the overall security of the evaluated environment.