risk-management
NIST
cybersecurity
Identification and Risk Assessment in the NIST Framework
It's time to dive deeper into one of the most important parts of the NIST cybersecurity framework: the first function, which is the identification and assessment of risks within an organization.
At this stage, we identify potential threats that may affect information assets, as well as existing vulnerabilities in the systems and processes of an organization. To do this, we carry out processes such as risk analysis, security reviews, and vulnerability assessments.
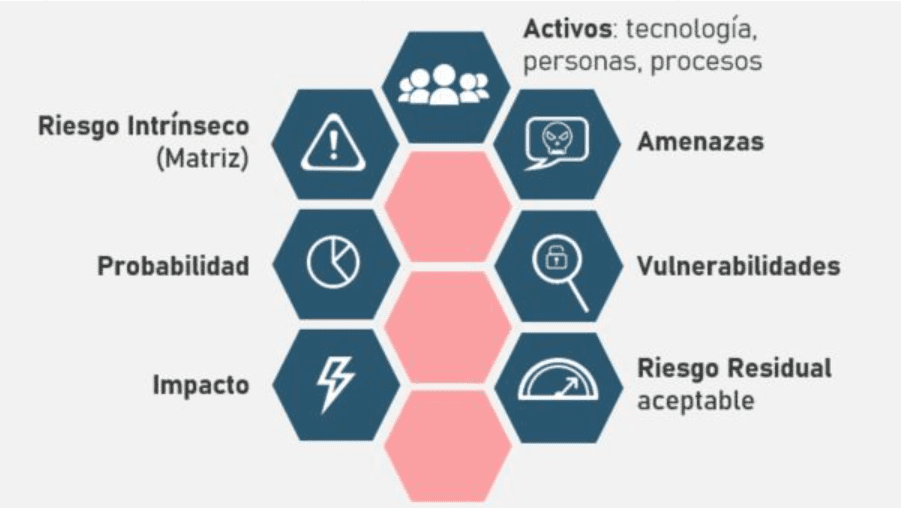
Let's explain in more detail what each process involves:
- Asset Identification and Classification Process
In this stage, we focus on identifying and classifying an organization's assets. This allows us to determine which assets are the most important and valuable. These can include confidential data, network infrastructure, applications, hardware, software, and any other element that is critical to the company's operations.
The first step is to conduct a thorough inventory of all information assets, gathering detailed information about each asset such as its location or owner, its function, and its importance to the organization.
After compiling this inventory, it is necessary to classify the assets according to their importance and value to the organization. This asset classification allows us to prioritize security resources and efforts based on the importance of each asset. For example, the security approach for the organization's servers will not be the same as for guest network devices.
All assets should be included in this classification so we can determine:
- Which devices and systems are necessary for the organization's operations
- Which platforms or software applications are most required by the organization
- Which external information systems are essential for the organization's operations
- What are the communication routes and data flows necessary for the organization's operations
A common classification scale such as high, medium, and low is used to assign importance levels to assets. High-importance assets are those that, if compromised, could have a significant impact on the organization, while low-importance assets have minimal impact.
In some cases, our job as cybersecurity analysts is to carry out this inventory and classification in accordance with the organization's needs and objectives, as well as to manage these assets for current and future requirements.
- Risk Analysis and Impact Assessment
This part of the risk identification and assessment process focuses on understanding the impact that a security incident could have on the confidentiality, integrity, and availability of information.
Risk analysis involves identifying potential threats that could affect information assets, as well as existing vulnerabilities in the organization's systems and processes. It also involves understanding how these threats could affect the mission, function, image, reputation, assets, and individuals within the organization.
To achieve this, we can carry out various processes such as evaluating the organization's vulnerable assets and identifying and documenting those assets. To understand the scope of a threat, we can also turn to external sources to gather information on how to deal with such threats, for example: sharing information in cybersecurity forums and discussions.
Based on these analyses, we can determine priorities, risk tolerances, and other assumptions that best fit our requirements within the company.
These risk analysis and impact assessment processes are ongoing. As threats evolve and security environments change, it is necessary to regularly review and update these processes to ensure the organization is prepared to face new challenges.
- Vulnerability and Threat Assessment
Vulnerability assessment involves identifying weaknesses and security flaws in an organization's systems, networks, and applications. This can be achieved through penetration testing, code analysis, vulnerability scans, and configuration reviews. The goal is to identify vulnerabilities that could be exploited by an attacker to compromise the security of information assets.
This process also seeks to identify and understand potential threats that could affect an organization. This includes internal and external threats such as cyberattacks, malware, phishing, social engineering, natural disasters, among others. It is important to keep in mind that threats can evolve over time, so it is necessary to stay up to date on the latest trends and techniques used by attackers.
Once vulnerabilities and threats have been identified, their potential impact on information assets and the organization as a whole is assessed. This involves determining the likelihood that a vulnerability will be exploited and the impact it would have on the confidentiality, integrity, and availability of assets. This impact assessment helps prioritize mitigation efforts and make informed decisions about which security measures should be implemented.