data security
data loss prevention
Networking
cybersecurity
Network Security Policy
In today's connected world, businesses rely on computer networks for everything from daily activities to critical business functions. The primary goal is to reduce costs and increase convenience. This excessive dependence on the Internet has its downsides. Poor network security practices and inconsistency among different teams operating on a network leave the organization vulnerable to more network security threats.
To overcome this, businesses create a network security policy: a set of rules that must be followed throughout the organization to present a unified front against network security threats. Losses from network security breaches continue to increase each year, and without a strict network security policy, an organization only exacerbates them. Losses from cyber security incidents are expected to be $8 trillion in 2023 and projected to grow to $10.5 trillion by 2025.
What is a Network Security Policy?
A network security policy is a set of mandates for monitoring, managing, and enforcing security in your organization's network infrastructure. It details network security access controls, protocols to follow, and procedures to enact to keep the network protected from any activity that may threaten security.
Network security policies are comprehensive documents that cover various facets of an organization's network security. These policies are typically drafted and reviewed by management or contracted external services. Network security policies cover the following categories in detail:
- Guidelines for acquiring new devices or technologies.
- Rules to follow when accessing the network or making changes to it.
- Steps or processes to follow when a security breach occurs.
- Procedures for applying access controls to network devices.
- Definitions of user privileges and user access to authorized processes or services they can perform on the network.
Why is a Network Security Policy Important?
An effective network security policy is like the blueprint of a very complicated maze. The detailed guidelines it contains serve as a framework for maintaining a secure network, highlighting employee responsibilities in enforcing that security. A network security policy plays a crucial role in protecting your organization's network from both internal and external threats.
Without an adequate network security policy, there is no consistency in the security practices applied by different teams within an organization. This, in turn, can lead administrators to overlook vulnerabilities and security gaps, leaving them ill-prepared to defend against attacks and security breaches, resulting in greater losses.
How to Create an Effective Network Security Policy?
An effective network security policy must address the unique requirements of the organization's network infrastructure, reduce potential security risks, and ensure the safety and integrity of the organization's assets and data. Here are some best practices to consider when drafting your organization's network security policy:
- Assess existing security risks and vulnerabilities: It is essential to understand the threats your organization currently faces before creating a network security policy. With this information, you can create a policy that specifically addresses these threats.
- Implement security controls: Security controls are the measures taken to address identified risks and vulnerabilities. These steps include implementing firewalls, IDS and IPS; enabling access controls and data encryption; and, in some cases, better employee training.
- Define roles and responsibilities: Define who has access to what and what changes they can make on the network. This must extend to all employees, including IT staff, end users, corporate-level executives, and network security personnel.
- Summarize incident response practices: Establish incident reporting procedures, steps for responding to threats, and recovery steps. This includes creating an escalation path, establishing communication channels, and preparing reports for future audits.
- Create a review and audit process: Regularly audit and update the network security policy to ensure its effectiveness. Audits help you understand potential network vulnerabilities and prioritize them for improvement. Equipped with this information, you can better face emerging threats and address any new vulnerabilities before they create a lasting impact on your network's security.
Network Security Management
What is Network Security Management?
Network security management allows the administrator to manage a network comprised of both physical and virtual firewalls from a centralized location. Network security administrators need management solutions to gain a high level of visibility into network behavior, automate device configuration, enforce global policies, view firewall traffic, generate reports, and provide a unified management interface for physical and virtual systems.
Issues Addressed by Network Security Management
In today's complex network architecture and constantly changing threat environment, it is challenging for IT staff to maintain an effective security posture. Security administrative tasks include supporting an ever-growing matrix of users, devices, locations, and applications, meeting compliance obligations, enabling new services, optimizing performance, ensuring access controls and security mechanisms, and troubleshooting on demand. Any configuration error can make the network vulnerable to sophisticated threats and regulatory non-compliance.
To address these issues, network administrators must consistently deploy security policies across their network. However, network infrastructure can have thousands of accumulated firewall policies over the years. Often, these rules are disorganized, duplicated, outdated, or conflict with new rules, inadvertently affecting network performance and security.
The following illustration represents a typical company scenario, where the IT department must pay attention to network security management:
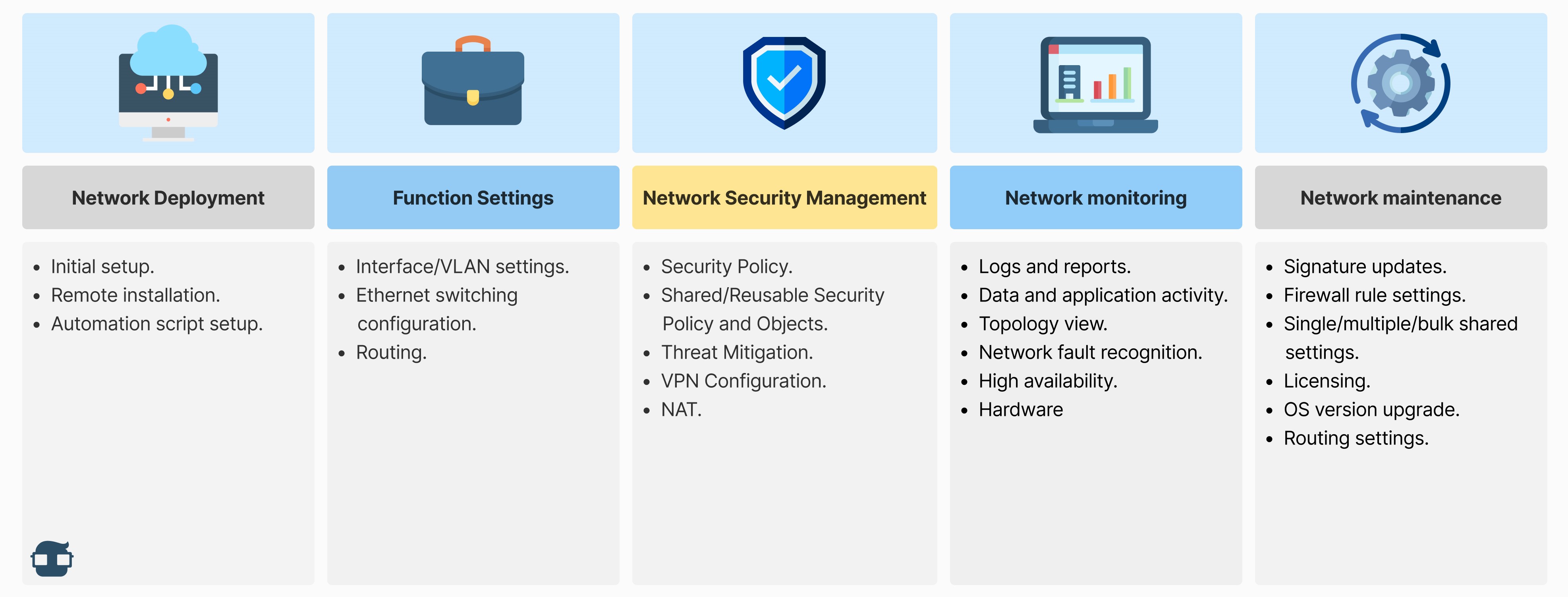
- Network security management reduces manual tasks and human errors by simplifying administration with security policies and workflow tools through a centralized management interface.
- Network security management can reduce risk across the network and protect data by obtaining threat intelligence, network vulnerabilities and their relevance, assessing possible options to block the attack, and intelligence to support decisions.
- Policy management is improved by unifying common policy tasks within a single interface, automating the operational workflow of policy change, such as compliance audits and management of multiple firewall vendors. This simplified and automated security policy management enables IT teams to save time, avoid human errors, and reduce risk.
How Does Network Security Management Work?
Network security management provides complete network visibility and generates data for assets (groupings and classifications), firewalls, applications, ports, protocols, VPNs, and security policies and vendor devices. This information allows you to delve into the details of individual devices and analyze them. The data is translated into intelligence that decrypts security transactions into malleable and actionable information in the form of policy creation. Updated policies are distributed to enforcement points (firewalls), ensuring network protection.
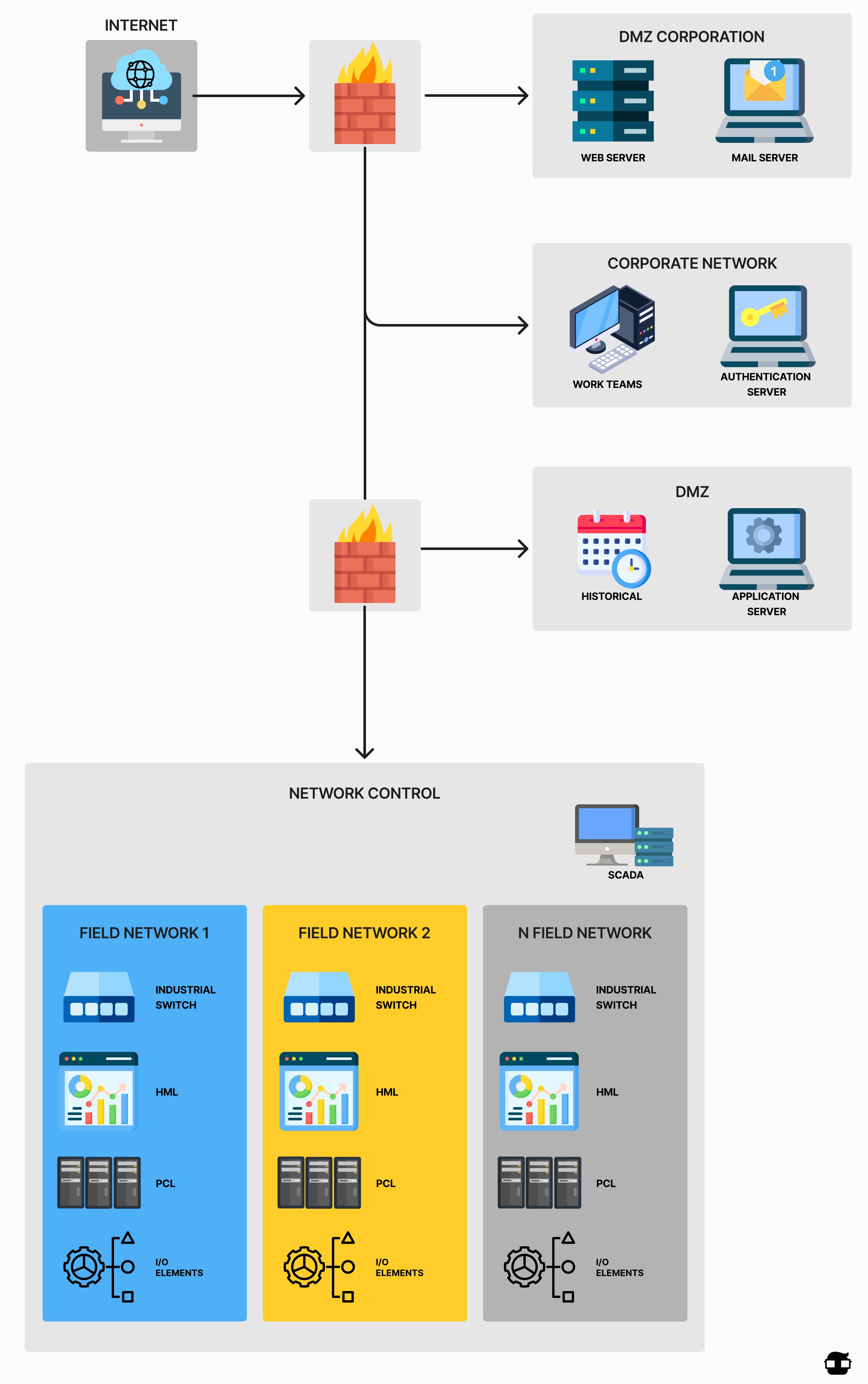
Network Security Architecture
Base Architecture for Control Systems
The base architecture selected is based on the proposal offered by the IEC 62443 standard. It defines different zones associated with the levels into which an industrial control system is divided. The base architecture presents segmentation based on firewalls to separate the control and corporate zones, also having two DMZs for information exchange between both zones. The following proposed architectures present security architectures to ensure communications and devices located on the control side of the network. Corporate security is not considered in this study as it is outside its scope.