penetration testing
cybersecurity
Identify Vulnerable Systems and Services during pentesting
Identifying vulnerable systems and services is a critical step in penetration testing and security assessment. Here are the general steps and some common tools used to accomplish this task:
- Port Scanning: Use tools such as Nmap, Masscan, or Unicornscan to identify open ports on the target system.
- Service Identification: Examines services on open ports using techniques such as fingerprinting to determine the version and type of service.
- Search for Known Vulnerabilities: Uses vulnerability databases, such as the NIST National Vulnerability Database (NVD) or Common Vulnerabilities and Exposures (CVE), to search for known vulnerabilities associated with identified service versions.
- Active Scanning and Configuration Analysis: Uses tools such as Nessus or OpenVAS to perform vulnerability scans and analyze configurations for known weaknesses.
- Selective Exploitation: If explicit authorization is available, controlled exploitation of vulnerabilities can be attempted to confirm their existence and assess potential impact.
- Log Analysis and Documentation: Examine system and service logs to identify anomalous activity, and document all identified vulnerabilities.
💡 It is critical that all activities are performed with the consent of the system owner and in compliance with applicable laws and regulations. In addition, the results must be documented and communicated to the client ethically and professionally.
Vulnerability Assessment: What It Is and How To Do It
A vulnerability assessment analyzes and estimates the risks of security weaknesses in an organization's systems. More than 180,000 security vulnerabilities are known, and new ones are discovered every year. With so many potential breaches in infrastructure and so many possibilities for attacks on systems, it is not surprising that cybercrime has increased considerably in recent years. However, when conducted regularly and correctly, vulnerability assessments can act as a preventative measure against these growing security threats. Consider that even with top-notch security defenses, an organization's information and security systems can still be attacked, hacked, or hijacked by cybercriminals.
What Is a Vulnerability Assessment?
A vulnerability assessment is the process of reviewing and estimating all possible security weaknesses in an information system's infrastructure. This type of assessment is used to identify, prioritize, and mitigate vulnerabilities and to minimize potential security threats. These assessments also uncover and analyze vulnerabilities within the organization's physical environment. The objectives of a vulnerability assessment can be broken down into three main ideas:
- Identify all vulnerabilities.
- Documenting vulnerabilities for future identification and.
- Guide developers who create solutions for these threats.
Vulnerability assessments should be performed regularly, especially when new equipment is installed, ports are added, or services are introduced. In addition, vulnerability assessments can prevent system attacks on devices - new and old - due to threats such as:
- Injection attacks, including XSS attacks and SQL attacks.
- Weak default configurations, such as easy-to-guess admin passwords and usernames.
- Malware and malware attacks.
- Faulty authentication tools and devices.
- Unencrypted data.
💡 For at-risk organizations - such as banks, government systems and those with access to personal information, such as healthcare facilities - vulnerability assessments can help identify and reduce weaknesses before they are exploited by hackers.
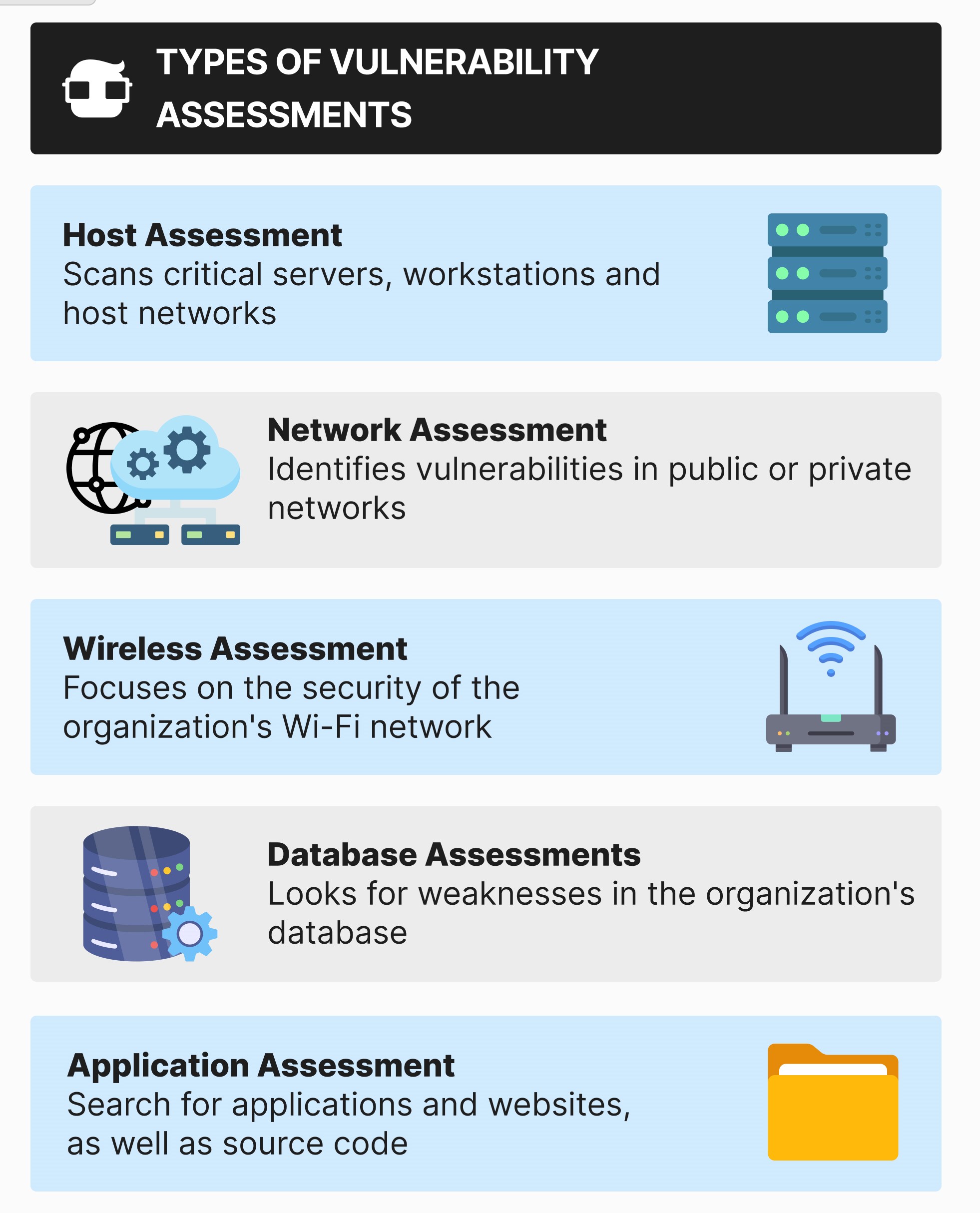
Types of Vulnerability Assessments
Different types of vulnerability assessments use individual tools to identify system and network weaknesses. Stand-alone systems may require several types of assessments to identify all of their potential vulnerabilities.
- Host assessment: A host assessment focuses on servers, workstations, and other critical network elements. Although ports and services can be scanned with network assessments, the host assessment can also be used to identify the network's vulnerabilities, A host assessment is capable of reviewing patch history and configuration.
- Network assessment: A network assessment is used to identify potential vulnerabilities as a whole. It can be performed for both wired and wireless networks; these assessments help prevent security attacks targeting private and public networks, as well as accessible information from connected computers.
- Wireless assessment: The purpose of a wireless assessment is to analyze an organization's Wi-Fi network. Insecure wireless networks, including those with unapproved access points, can lead to attacks on an organization's entire infrastructure. These assessments also verify that an organization's network is securely configured with HTTPS.
- Database assessments: Database assessments scan an organization's stored data set for vulnerabilities. Malicious attacks, such as SQL injections, often target databases with misconfigurations, unregistered databases, and those with weak development tests (DevTests). These assessments also help organizations identify where personal information needs to be classified in an infrastructure.
- Application assessment: An application assessment scans web apps, sites, and source code for incorrect software downloads, broken configurations, and other security vulnerabilities. They are usually automated scans of front-end code and infrastructure.
Vulnerability Assessment vs. Penetration Testing
Vulnerability assessments and penetration tests are not the same thing, but since vulnerability assessments can also include a penetration test, the two can easily be confused. These dual assessments are often referred to as vulnerability assessment/penetration testing or VAPT, but they do not always have to be performed together.
Penetration testing is used specifically to find weaknesses in personnel, the organization, and its procedures and is an additional process that can be added to the entire vulnerability assessment. Penetration testing also attempts to create damage to an application or network by exploiting potential weaknesses in a controlled environment to demonstrate that vulnerabilities exist.
Penetration testing uses both automated and manual maneuvers to test for vulnerabilities. Those weaknesses are then analyzed by researchers to create specific protections and defenses. However, they are not sufficient on their own and must be followed by a full vulnerability assessment.
Performing a Vulnerability Assessment: Steps for Identifying Vulnerabilities
If a vulnerability assessment is performed without a penetration test, there are four main stages.
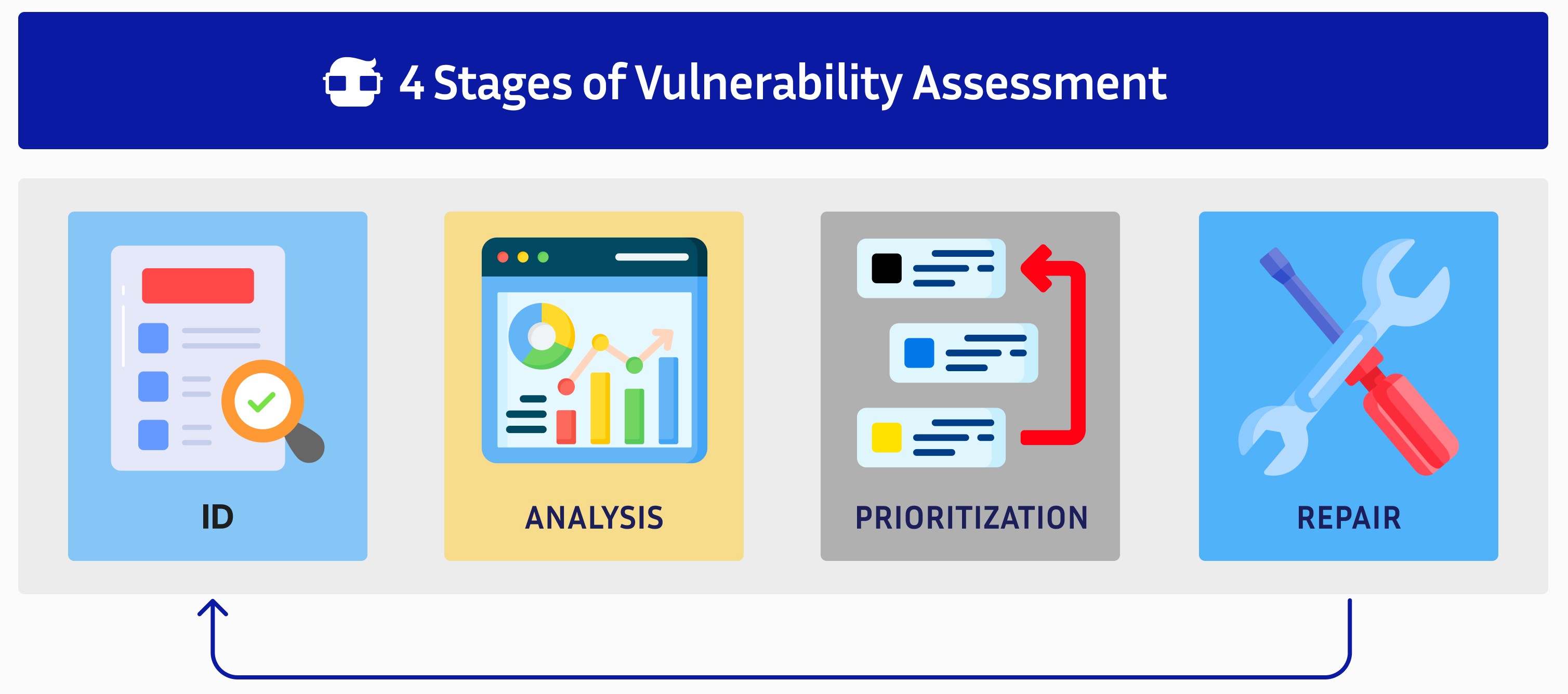
Identification of Assets and Vulnerabilities
Identification is the first stage when performing a vulnerability assessment: before starting a scan, you must identify scannable assets, including popular tools, such as mobile devices, Internet of Things devices, and cloud-based programs. The infrastructure is then scanned by automated tools or manually by security analysts. A vulnerability assessment report is produced that describes the weaknesses identified.
Analysis
In the analysis stage of a vulnerability assessment, the goal is to find the origin and cause of each weakness. To identify the root cause, the infrastructure components that are responsible for each vulnerability must be further verified and analyzed. The scanning stage also checks for improperly installed or updated systems.
Vulnerability scanners-and their built-in databases of known vulnerabilities-can pinpoint potential system weaknesses, vulnerable devices, and risky software to help complete this stage. Since many vulnerabilities are publicly reported, they can be quickly identified and their root cause analyzed.
Risk Assessment and Prioritization
After you have identified and analyzed your organization's vulnerabilities, it is time to conduct a risk assessment and determine prioritization. The first stage should provide assessment reports, which can be used to determine which vulnerabilities are most dangerous to an organization. During a risk assessment, security analysts assign each vulnerability a severity score; higher numbers indicate weaknesses that should be addressed as soon as possible. Vulnerabilities are ranked based on some factors, including:
- The systems affected.
- The information at risk.
- Ease of attack or compromise.
- Potential damage to the infrastructure and the organization.
Remediation and Mitigation
The final stage in conducting a vulnerability assessment is remediation and mitigation. This stage is typically performed by security professionals and operations teams and focuses on finding ways to alleviate weaknesses while developing plans to decrease the likelihood of vulnerabilities reoccurring. When creating remediation and mitigation plans, practitioners should focus on two factors:
- Gravity: After prioritization, teams should address the most severe vulnerabilities first. Over time, they should be able to create and publish fixes for each vulnerability detected, but early remediation focuses on the most dangerous ones.
- Vulnerability exposure: Determining whether a vulnerability is public-facing or Web-facing should also be a primary concern for remediation professionals. Internet-facing vulnerabilities are easier for cybercriminals to exploit, so these weaknesses should be mitigated first, followed by employee-owned devices and those that store sensitive information.
If system patches or vulnerability fixes are released, the vulnerability assessment process should begin again. It is important to run an assessment when any type of new system or patch is installed to quickly identify, analyze, prioritize, and remediate any new vulnerabilities that may arise.
Vulnerability Assessment Tools*
Vulnerability assessment tools are often automated processes that can be used by anyone from cybersecurity experts and threat hunters to worker logging on at home. These tools scan systems for existing vulnerabilities and new unreported weaknesses. In addition, each assessment tool has a specific purpose based on the type of assessment it is to perform.
Types of vulnerability assessment tools:
- Web application scanners.
- Protocol scanners.
- Network scanners.
- External and internal vulnerability scanners.
- Environmental scanners.
In addition to the type of assessment that each tool performs, they have their characteristics that the user must take into account. When choosing an assessment tool, keep these characteristics in mind:
- Frequency of updates.
- Ability to minimize false positives and negatives.
- Ability to integrate with other assessment and security tools.
- Actionable results.
While vulnerability assessments are a necessary part of the cybersecurity process, there are additional precautions you can take to keep your infrastructure better protected. Investing in a VPN can help protect your browsing on public and private networks, while an antivirus can help keep both mobile and desktop devices secure.
Identifying Operating Systems and Services
As we can see, Nmap allows us to detect ports that are listening on an IP or range. Later we will also see how other scanning techniques can be defined. In addition, Nmap allows us to try to identify which technology (product, version, etc.) is behind an open port, or even the operating system installed on a server, with the -O and -sV parameters. This detection is based on the “signature” (fingerprint) of the responses given by the service to certain calls.
1sudo nmap -O -sV 192.168.1.1
In this case, not only do we know that this machine has certain ports open. It also tells us that it is a Linux and the versions of the various ports that are listening so that this information can be used to exploit vulnerabilities on unpatched versions, etc.
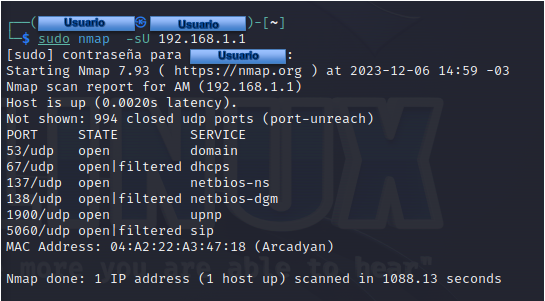
Utilizing more scanning techniques
By default, Nmap uses SYN as a scanning technique. It is a fast and not very intrusive/detectable technique, but sometimes, it supports in total of 12 different techniques that we can define as parameters, as we can see in the tool's user manual. For example, if we want to do a scan based on UDP calls, we can make a call of the type:
1sudo nmap -sU 192.168.1.1
 User
User
Searching for Vulnerabilities With Nmap
While there are more “comfortable” and specific tools for searching for vulnerabilities, such as Nessus, or suites such as Metasploit that consolidate several tools, nmap also allows us to perform vulnerability analysis.
To do this, it uses a series of Lua scripts that are located in a path on our machine (in the case of Kali, in /usr/share/nmap/scripts/ ) and can be invoked with -script or its equivalent -sC.
Scripts can belong to one or several categories, so we can ask Nmap to evaluate, for example, all the scripts of a category against a host. There are some particularly interesting categories such as “vuln” (scripts dedicated to detecting vulnerabilities in the target), “exploit”, etc.
For example, if we want to scan the vulnerability category scripts against a host:
1nmap --script vuln scanme.nmap.org
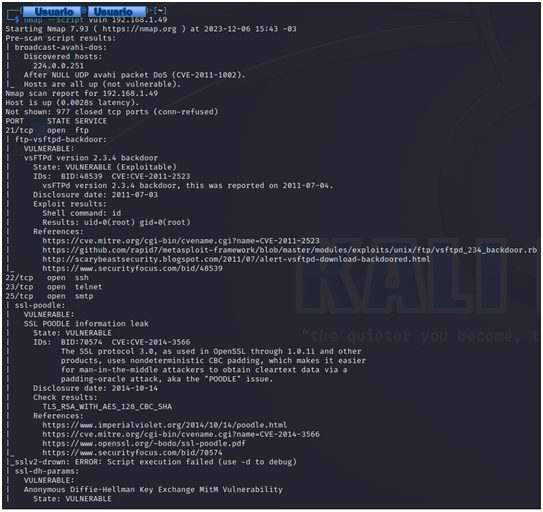
As we can see, the script has detected many vulnerabilities. If we analyze the scripts, we will see that many of them will serve to exploit these vulnerabilities. In short, Nmap even includes interesting options for assessing vulnerabilities and even launching exploits, although there are other tools commonly used for this purpose.
Cautions
If and when we are going to use this type of program or tools, we must be clear that this can be dangerous for users. By scanning the packets that are transported over the network, we can have a lot of information in our hands. This makes it easier for data leakage to occur. Therefore, they should always be used appropriately and for legal purposes. Although the use of this type of application is not illegal, on the contrary, we must be careful with their use.
We have a huge amount of programs to perform vulnerability scans on our networks, computers, web services, and other services that incorporate the servers. Depending on what we are doing, we will have to use one scanner or another.
Vulnerability Databases
An important aspect is that the various IT security management solutions use these databases to support us in mitigating the risks of potential cyber-attacks. The databases you will find below, and others, are the main contributors to security management solutions. Before there were standards such as CVE and CVSS, the different solutions had their databases, with a great disparity of criteria for naming them, classifying their criticality, and other aspects.
CVE (Common Vulnerabilities and Exposures)
It is one of the most reliable sources when identifying, analyzing, and certifying a vulnerability found. Each of the vulnerabilities present in this database has a CVE number. The latter is provided by a group of specialized authorities of the CVE working group. But why would a vulnerability have an identifying number? This allows the handling of information about the vulnerability to be much more reliable, avoiding ambiguities or erroneous data that could damage the information about the vulnerability in question. This same number allows it to be easily identified and evaluated by the different security tools, such as the SIEM, which are the Security Information and Event Management Systems so that they can facilitate the implementation of actions to mitigate risks.
Since its foundation in 1999, CVE has become a standard when it comes to making any vulnerability public. As we have already mentioned, the various security tools implemented, especially in corporate networks, people specialized in computer security, and even the public can communicate more fluently. The latter concerns what a certain vulnerability consists of and its impacts. We are sure that at some point, you have read some news, publication, or tweet about one or more vulnerabilities. In many cases, they refer to the CVE number as a form of secure and reliable backup for the information presented.
CERT Vulnerability Database
Another database, this time from the prestigious CERT (Computer Emergency Response Team). It provides information regarding any software vulnerability. The data included are technical details, possible forms of remediation, and which manufacturers are affected. Many of the records found are the result of the efforts of individuals. Also, people working outside of government institutions to make available all the information found.
Consequently, several of the records could give the impression that there is a lack of depth concerning one or more data. This is why CERT itself recommends referring to government institution databases such as the NVD, which we will discuss below.
NVD (National Vulnerability Database)
As we commented recently, this database is linked to a government institution. It is the NIST, which is the National Institute of Standards and Technology. It is an extensive repository that hosts data regarding vulnerabilities that have been managed using the SCAP protocol. Its acronym stands for Security Content Automation Protocol.
The direct advantage of this data is that it makes it much easier to automate repetitive tasks of vulnerability management, measurement of security indicators, and compliance. In addition, you will be able to find everything related to security flaws found in all types of software. You will also learn about configuration errors, the name of the affected manufacturer, and the potential impacts of the vulnerability or bug found.
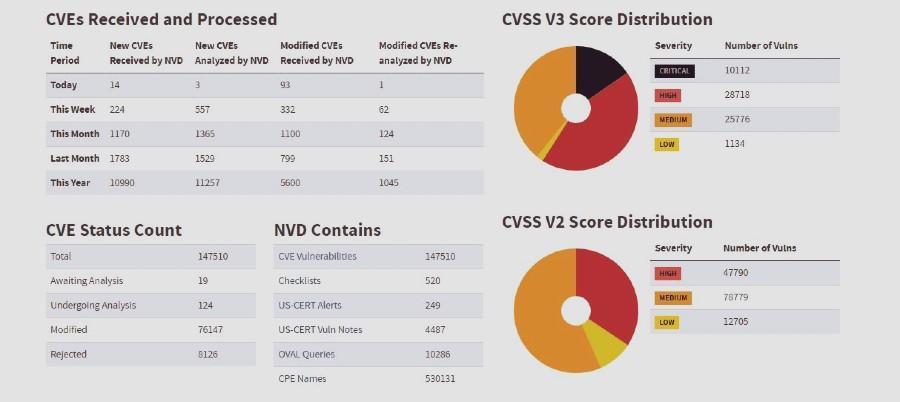
A very important detail is that, when you enter the statistics panel, you will find the vulnerabilities listed with the CVE classification, which corresponds to the first database we have cited. This means that practically every vulnerability cited in CVE has extra support from the national database. Although this is a U.S. government institution, it is one of the most consulted sources for the latest vulnerabilities.
On the other hand, this panel shows a couple of graphs based on CVSS. This stands for Common Vulnerability Scoring System. This is an open standard used to measure the severity of each of the vulnerabilities found. There are four possibilities or levels: low, medium, high, and critical. It is concluded that a vulnerability has a certain level based on a series of metrics. The standard, as well as all the databases mentioned above, is freely available to anyone interested.